Tech
What is a Network Management Tool, and Why Use One?
It is vital to guarantee the effectiveness and dependability of network infrastructures in the constantly changing field of information technology nowadays. With the use of

It is vital to guarantee the effectiveness and dependability of network infrastructures in the constantly changing field of information technology nowadays. With the use of
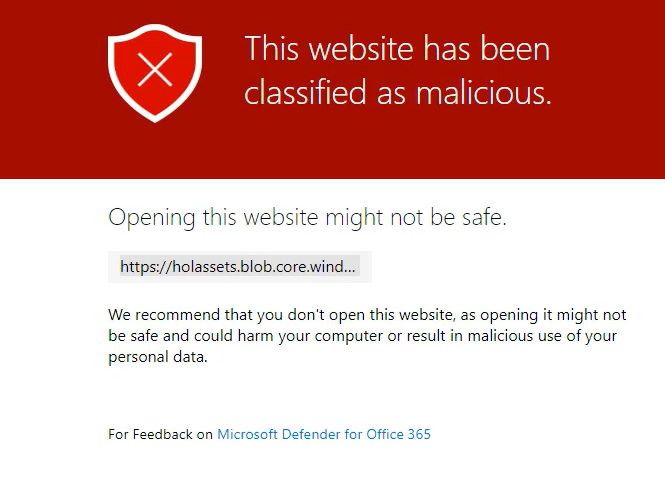
Safe Links policies are a powerful feature in Defender for Office 365. They allow you to leverage a virtual sandbox for URL scanning of inbound email messages in mail flow. This includes time
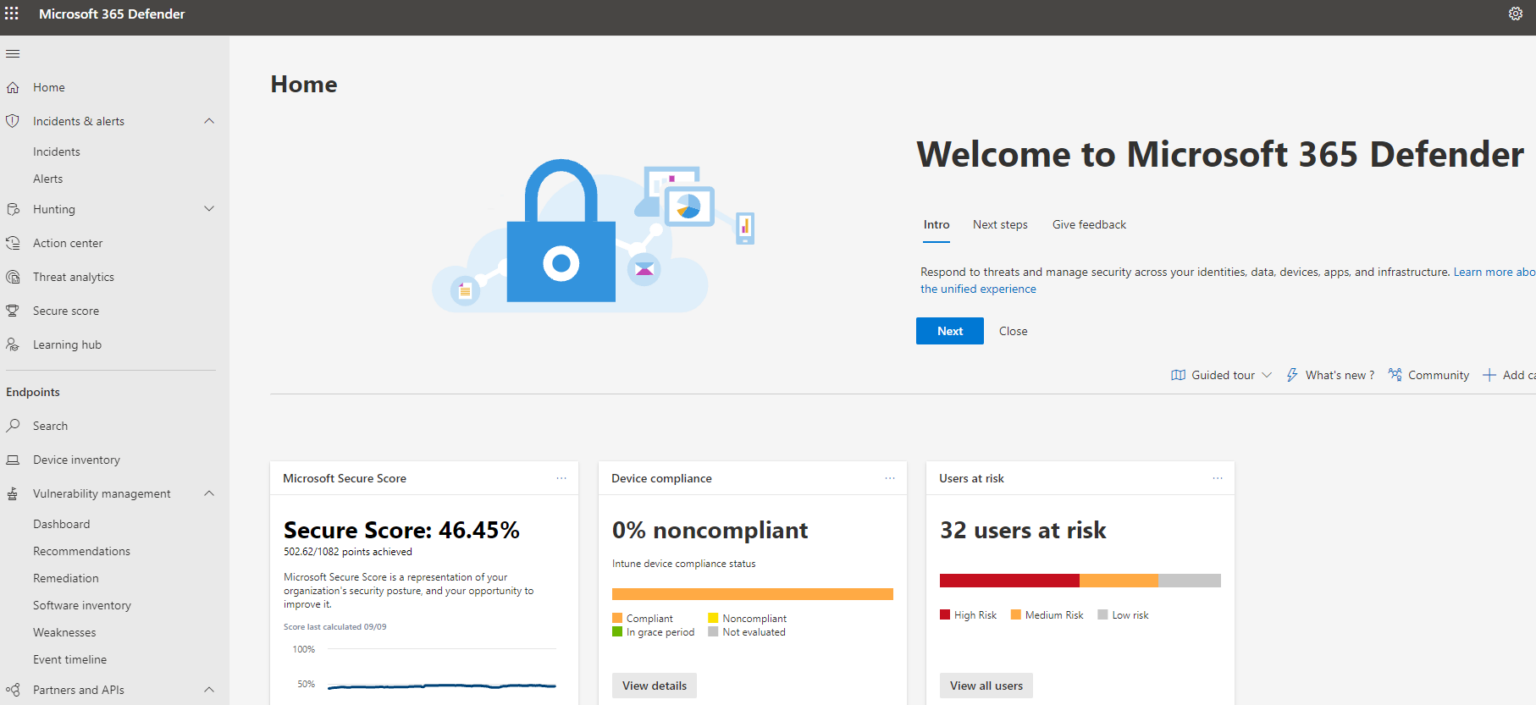
Microsoft recently announced that they are going to start to automatically redirect anyone going to the legacy “security and compliance admin center” to the newly