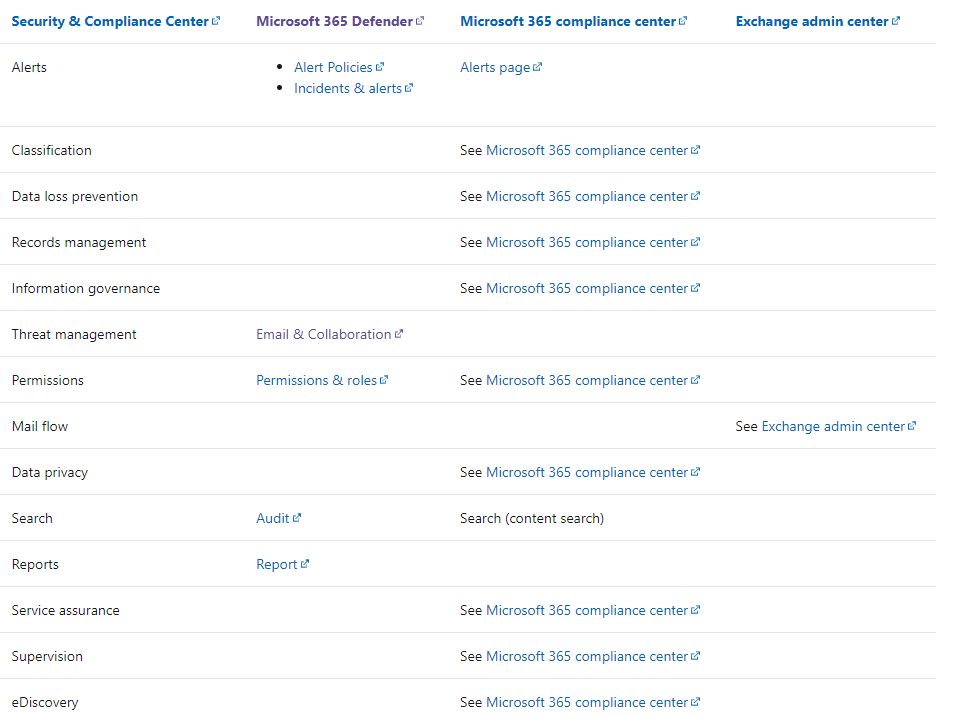
Microsoft recently announced that they are going to start to automatically redirect anyone going to the legacy “security and compliance admin center” to the newly rebranded Defender Security Center (located at security.microsoft.com). Microsoft Defender is an integrated experience of Microsoft’s suite of security services spanning Defender for Identity, Defender for Endpoint, Defender for Office 365, and Cloud App Security. Over the years Microsoft had many different portals to access security related services but now they have unified these portals under security.micorosft.com. In this article I am going to walk you through an overview of this rebranded portal.
Microsoft Defender Overview
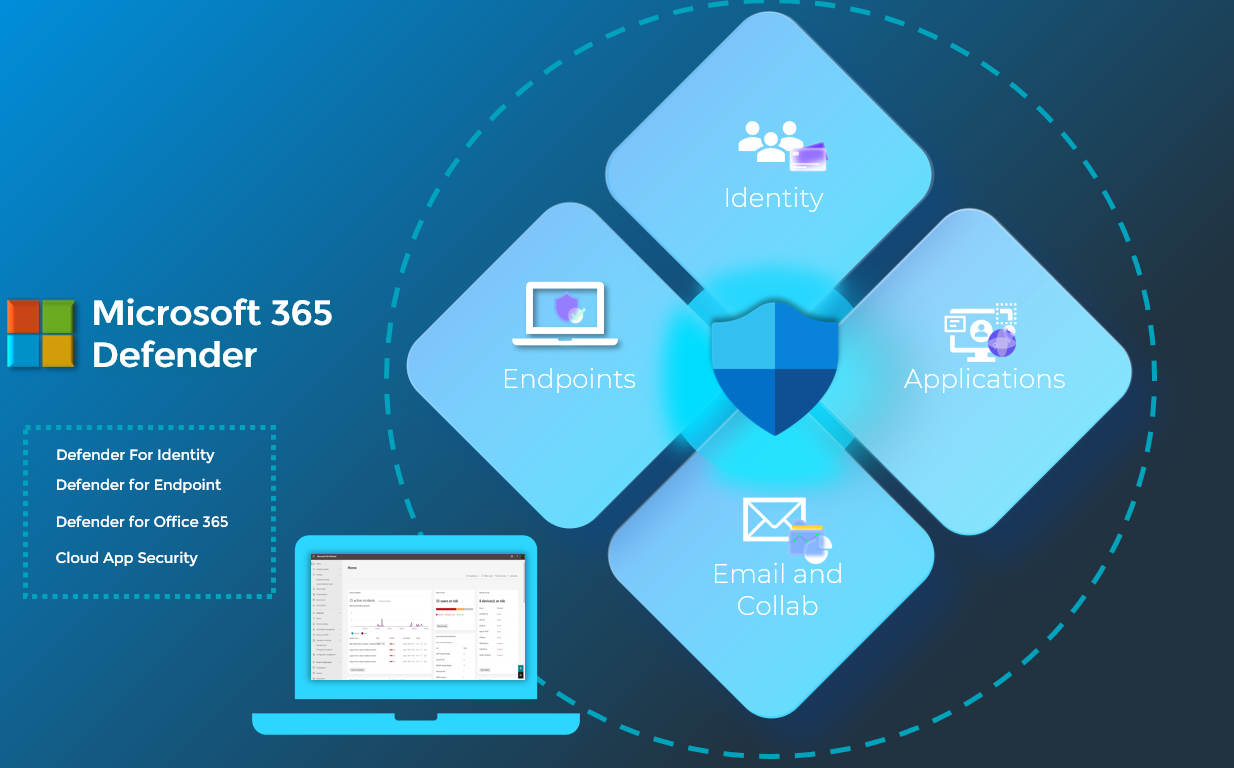
Microsoft 365 Defender is a unified pre- and post-breach defense suite that natively coordinates detection, prevention, investigation, and response across endpoints, identities, email, and applications to provide integrated protection against sophisticated attacks. Microsoft has recently unified various management portals for Defender for Identity, Defender for Endpoint, Defender for Office 365, and Cloud App Security for an integrated solution. One of the largest benefits is its ability to automatically correlate alerts across these domain and perform automated investigation/remediation.
Left-Hand Nav
Depending on what licensing you have within your tenant, the options available to you on this left hand nav might be a little different. I am in a tenant here that has Microsoft 365 E5 so it has access to the security suite that I will be walking you through today. I will not be covering all tabs here today as part of this initial introduction but I will be popping into the ones I feel like are the most important.
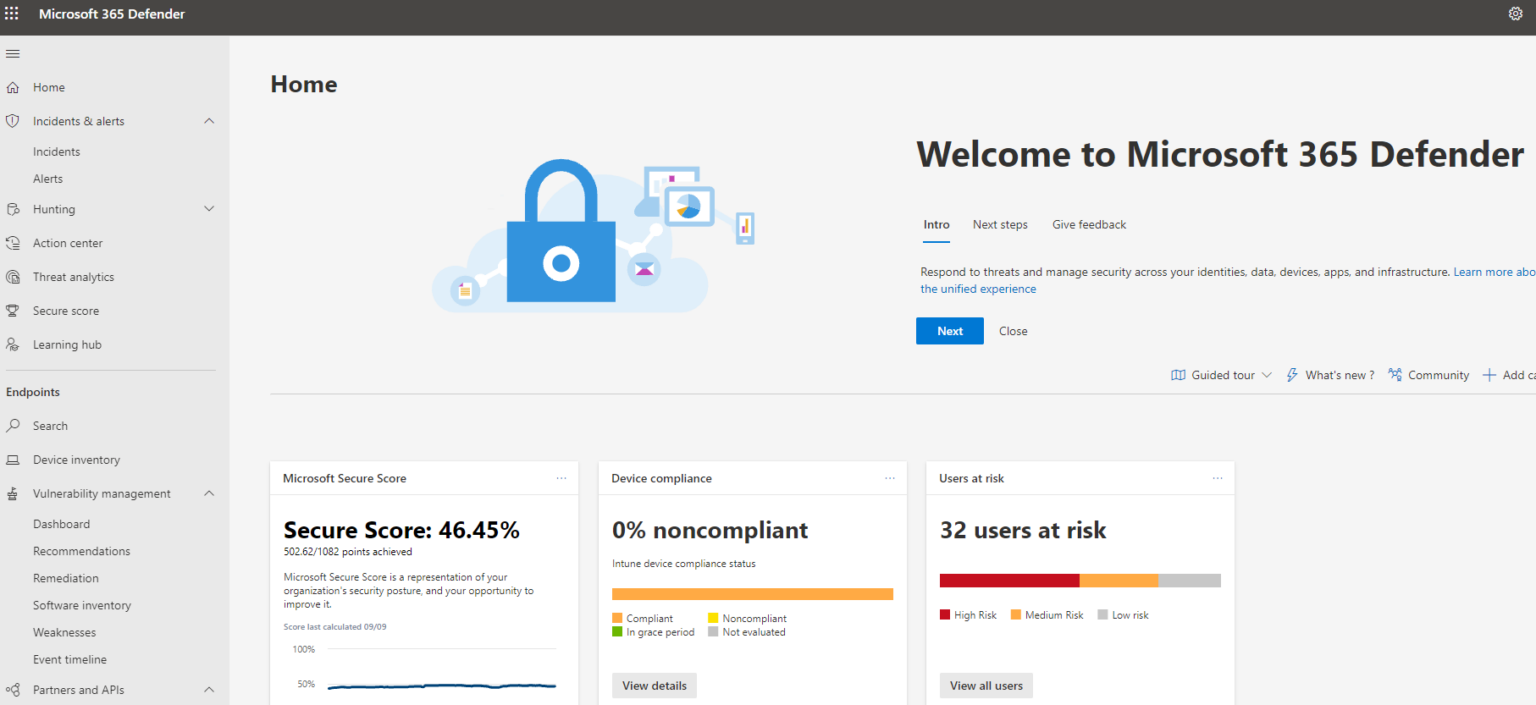
Dashboard
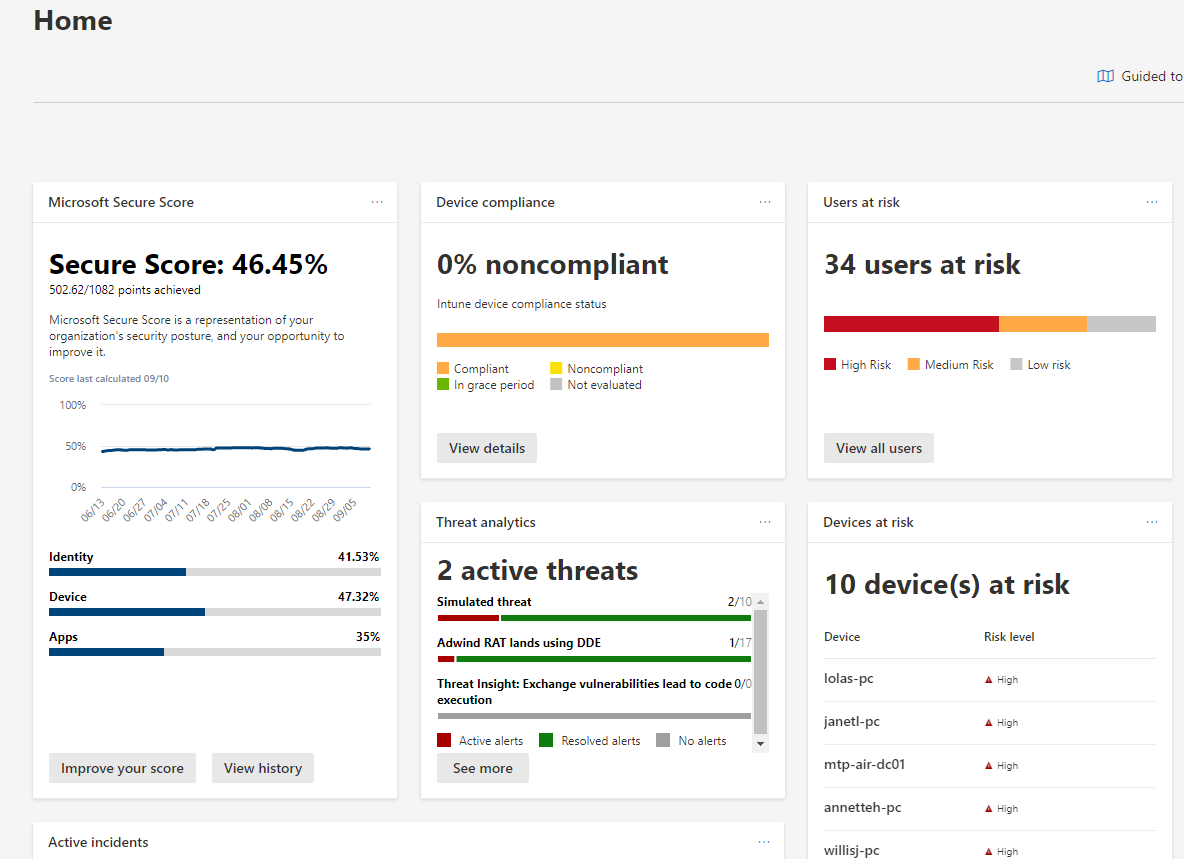
Starting off with the dashboard here, you can see key insights across identities, devices, email, and applications. The dashboard is completely customizable and each card can take you into another part of the security center to access more information about the topic.
Incidents and Alerts
Plans that show this tab:
- Defender for Office Plan 2
- Defender for Endpoint
- Office 365 E5
- Microsoft 365 E5
- EMS + E5
The incidents and alerts section is probably the most powerful section in my option. This is the location that correlates signals across the suite of security offerings and consolidates them into incidents. Clicking into these incidents brings you into a page where you can see things like timeline, scope and all the evidence that made up the incident. The service is also tagging these events with a severity score to help you with the prioritization of response. This kind of correlation would take days if not weeks in some cases but its all done in an automated fashion for you. Speaking of automation, the investigations tab allows you to see the automated investigations that were triggered from the alerts generated as part of the incident.
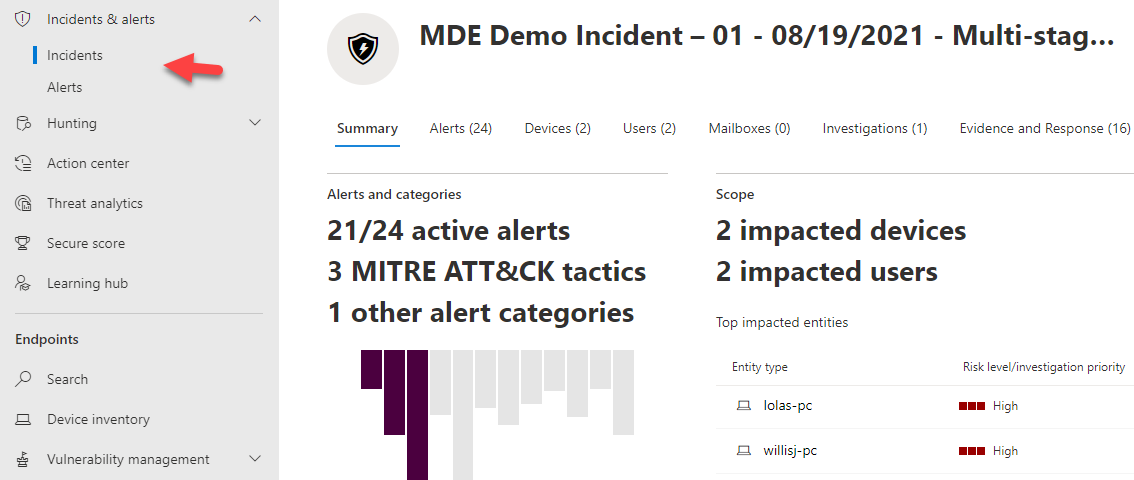
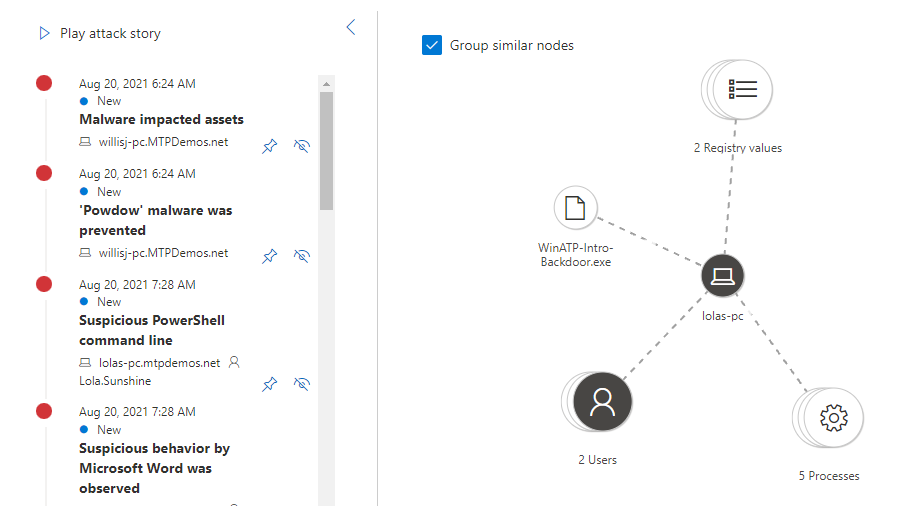
A graphical view can also be show that shows you the attack change. You can even play the attack story to see how things were correlated over time.
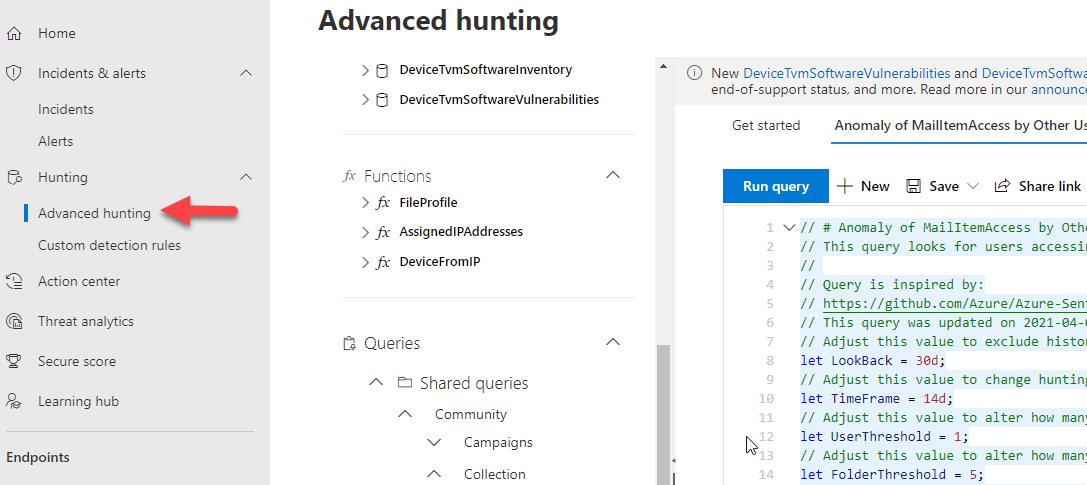
Advanced Threat Hunting
Plans that show this tab:
- Defender for Office Plan 2
- Defender for Endpoint
- Office 365 E5
- Microsoft 365 E5
- EMS + E5
Threat hunting is also available here so you can run advanced queries against your environment. Microsoft is providing a ton of automation on the detection and response capabilities and they provide this threat hunting tool so you can become more proactive with discovering threats in your organization. Premade queries are available to help you get started if you are unfamiliar with the KQL language.
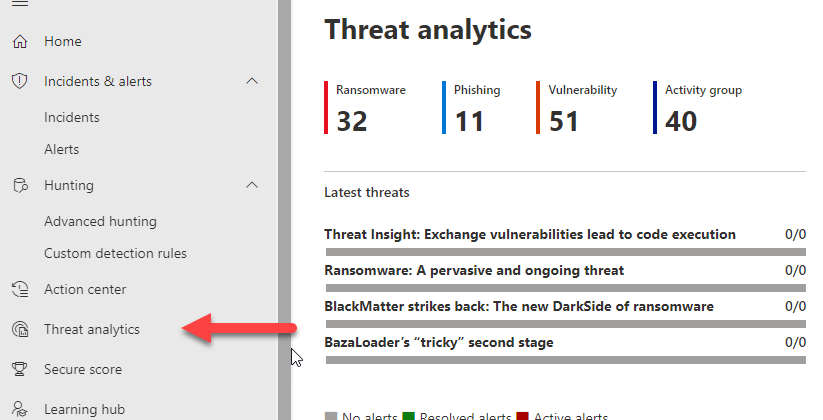
Threat Analytics
Plans that show this tab:
- Defender for Endpoint
- Office 365 E5
- Microsoft 365 E5
- EMS + E5
The Threat analytics pages is information coming straight from Microsoft’s security team. They are providing you information about the new threats in the market and showing you any assets within your organization that are exposed to these threats as well.
Clicking into one of these threats pulls up tons of details about the threat and well as some weaknesses in your organization that might lead to compromise.
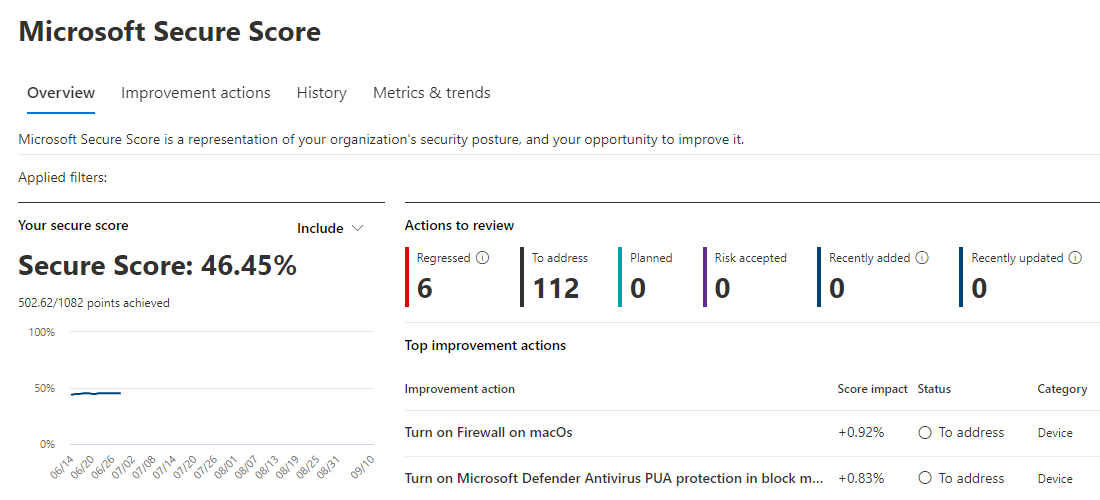
Secure Score
Plans that show this tab:
- All Business and Enterprise Plans
Secure score information shows you recommended actions to take within your environment across identities, endpoints, and applications. Each improvement action can be evaluated within your organization to help improve your score over time.
Learning Hub
Plans that show this tab:
- All Business and Enterprise Plans
The learning hub provides a ton of resources to help you get up to speed with the Defender suite of products. Since there has been so many changes recently, Microsoft wanted to provide a central location to get up-to-date information on their products.
Endpoints
Plans that show this tab:
- Defender for Endpoint
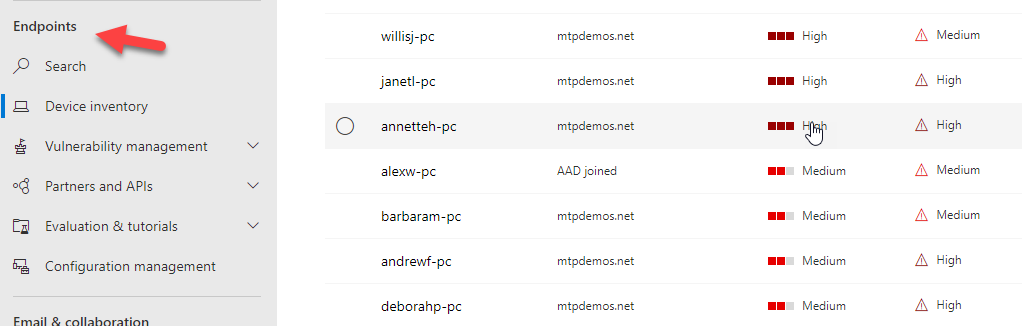
The next section here, Endpoints, is specifically focusing on the Defender for Endpoint Product offering. It includes a complete device inventory of all discovered devices on your network and also provide a separate Threat and Vulnerability dashboard.
Vulnerability Management
Plans that show this tab:
- Defender for Endpoint
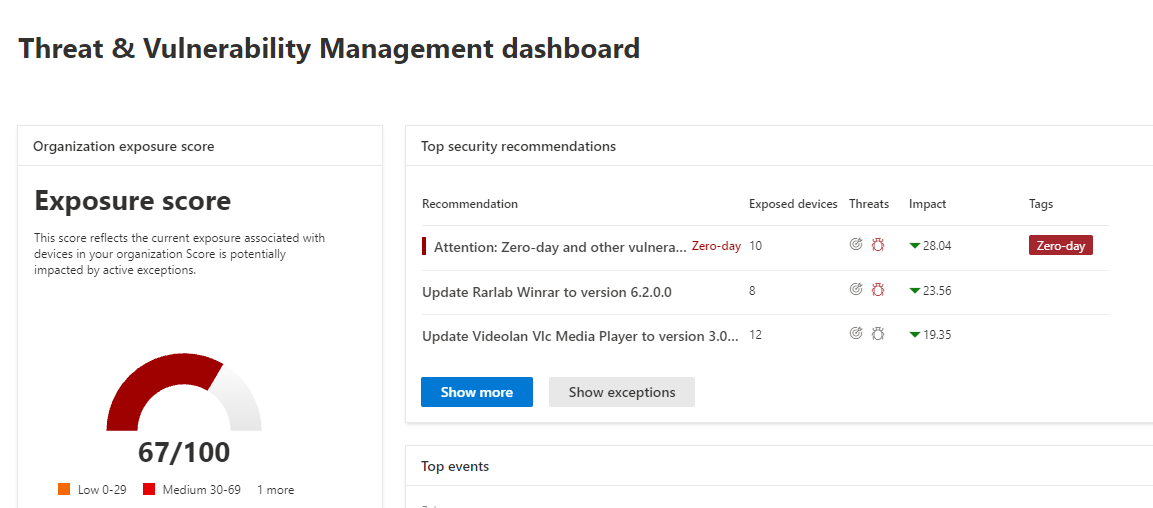
The Threat and vulnerability dashboard allows you to see key insights into the top vulnerabilities for your devices that may relate to the device configuration itself or vulnerabilities in software on that device. Known CVEs are published within the weaknesses section and you can see how many devices are exposed to that CVE.
Evaluation and Tutorials
Plans that show this tab:
- Defender for Endpoint
Simulations can be run against test devices that mimic common threats used in the market today. These simulations allow you to really get a feel for how Microsoft Defender triages and correlates incidents in this security portal so I highly recommend checking this section out.
Email And Collaboration
Plans that show this tab:
- Defender for Office365 Plan 1 and 2
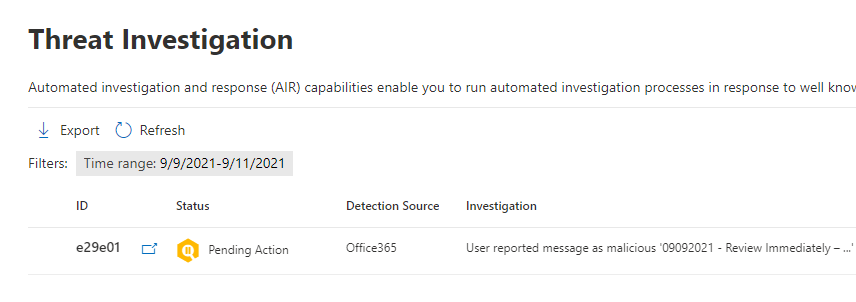
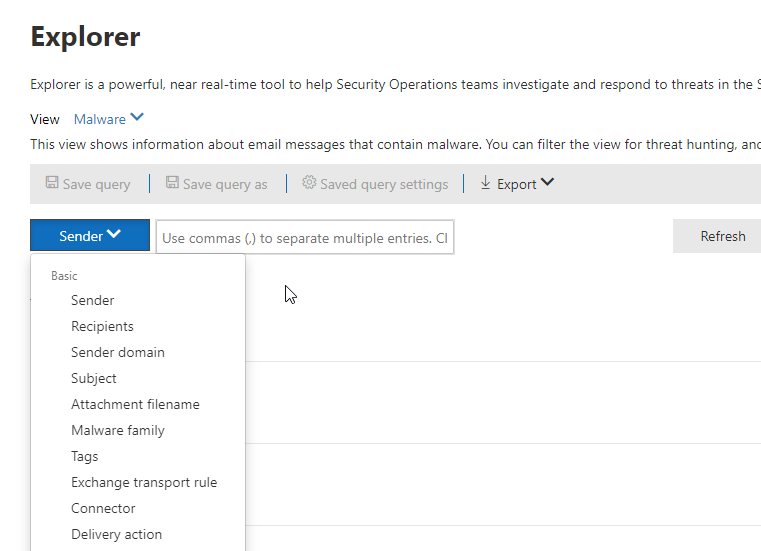
The next section, Email and Collaboration, relates to the Defender for Office 365 product line. Here you can see investigations that relate to incidents across email that were either automatically triggered by Microsoft, through user submission, or by an admin creating a new investigation through the explorer section. The explorer section allows you to save specific queries across various pieces of meta data and provides a ton of insight into what is going on within your organization.
Attack Simulation Training
Plans that show this tab:
- Defender for Office365 Plan 2
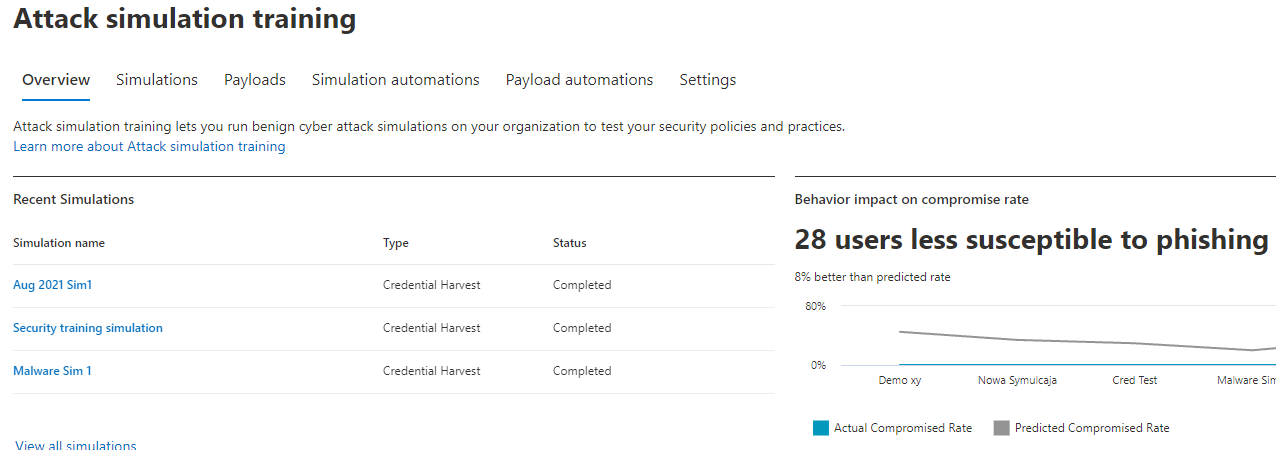
Attack Simulation Training can be conducted across the org to mimic common social engineering techniques used today. Security Awareness training can be assigned to users who natively fail the simulations.
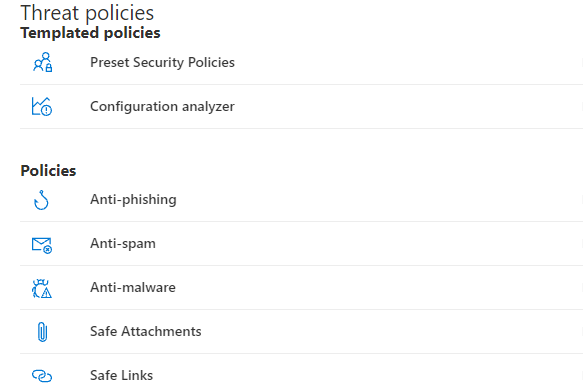
Policies and Rules
Plans that show this tab:
- Defender for Office365 Plan 1 and 2
Under Policies and rules, you can begin to define policies for anit-phishing, anti-spam, safe links, and safe attachments which helps prevent malware and phishing events. Microsoft even has predefined baselines that we will get to in later lessons that we could use if you need help on getting started.
More Resources
Finally under more resources, you have access to various admin portals that may include more functionality for a particular domain. The only one I want to call out here is Cloud App Security. While Microsoft has stitched in much of thex identity services within MCAS into the Microsoft 365 Defender portal, there is still many features related to applications that can only be conducted in that admin center at the time of this post
Final Comparisons
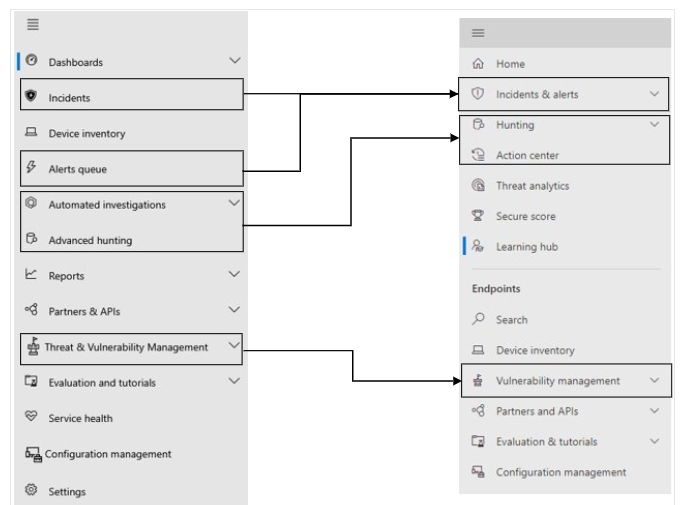
Microsoft has also created some more helpful diagrams to help with the transition complexity if you have been using other admin portals.
Defender For Endpoint Changes:
Defender for Office 365 Changes: