Digital data creation is exploding. This data is being stored and shared everywhere. Protecting important information across your digital estate, both in Microsoft’s cloud, on-premise, and in 3rd party apps is critical. Microsoft Information Protection is a comprehensive and integrated solution to help you discover, classify, label, and protect sensitive information within your organization.
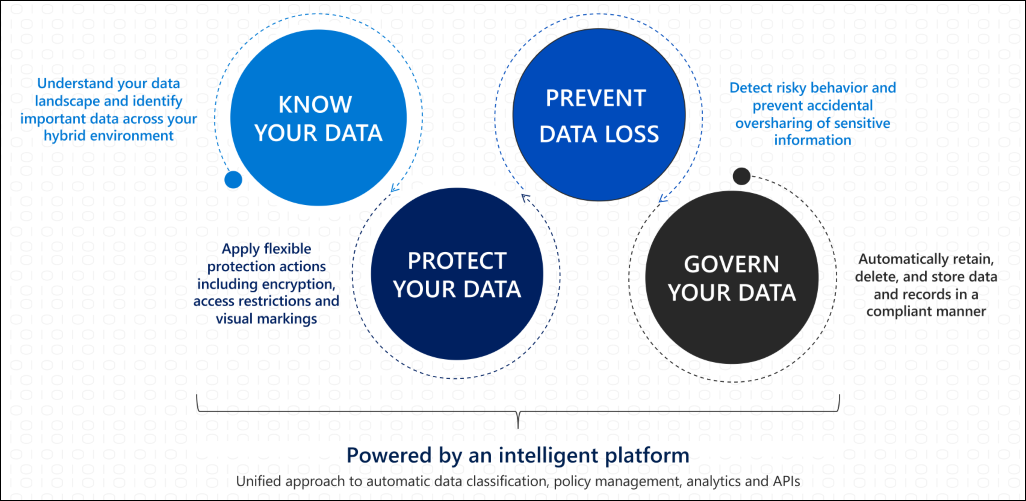
MIP includes many Information Protection and Governance solutions which help you solve for four key needs:
- Know your data
- Protect your data
- Prevent Data Loss
- Govern your data
Understanding the Threat Landscape
Before we get into more of the feature set of MIP, I first wanted to cover the threat landscape and why this solution is relevant. There are a variety of ways in which data can be breached in an organization. One of the most common ways is not malicious at all but accidental where an employee attaches a document or some type of sensitive content to an email that is sent outside the organization. There is also many new 3rd party applications that are being used within the organization that can lead to data exfiltration into unmanaged locations. Executives in a company may be targeted by malicious actors outside the company as they are seen to have access to the most sensitive content. These types of attacks could include phishing or spoofing attempts in efforts to get access to that sensitive content.
While we normally think of most malicious threats coming from outside the organization, we need to put protections in place to restrict internal users as well. A common example is a disgruntled employee who is leaving the company. Finally, many firms need to comply with regulations within their vertical such as HIPAA or FINRA. In order to remain compliant, information systems need to have some type of classification to help protect data and govern what users have access to certain content. The threat here is failing an audit because an organization does not have sufficient protections in place. A breach of this type of protection can lead significant fines for an organization such as PII being exposed for a hospital.
MIP Solutions Today
When we talk about information protection, there is a variety of solutions that bundle together to create data governance across solutions. Windows information protection allows you to protect corporate content on devices whether or not they are under IT’s management.
Office 365 DLP and Advanced Data Governance features allow you to detect sensitive content within Exchange, SharePoint, Teams, and OneDrive and apply certain controls such as encrypting the data and enforcing more restrictive protections like preventing that content from being shared to external domains.
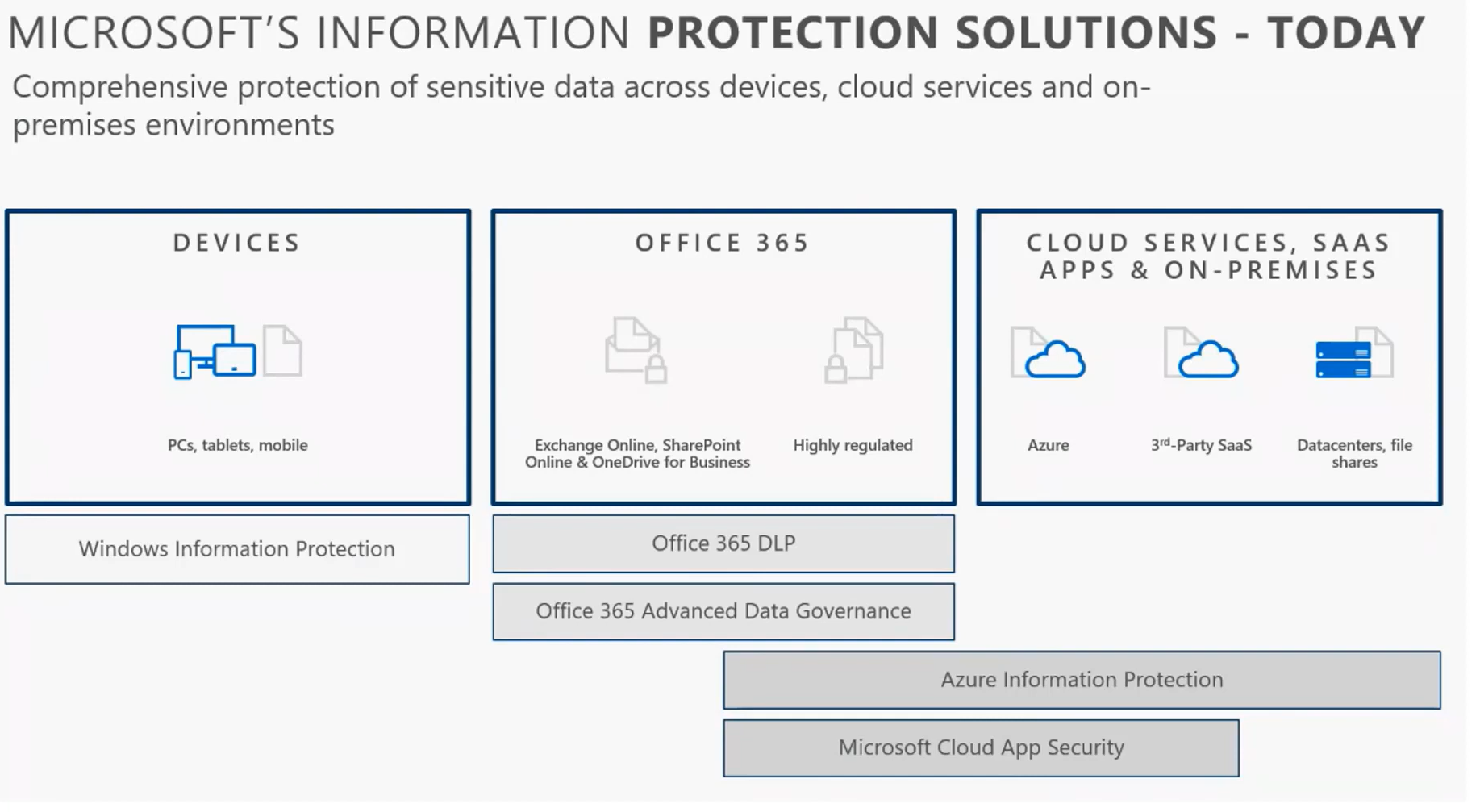
Azure Information protection is what I feel like MSPs are most familiar with which relates to the label taxonomy applied to content within the organization and the protections like email encryption. Paired with Microsoft Cloud App Security, it does allow you to extend your taxonomy into 3rd party applications outside of Microsoft’s cloud. In addition, it does extend this protection on-prem as well where you might have existing datacenters and file shares. This extension is very important for organizations slowly moving to cloud workloads.
Label Taxonomy Admin Experience
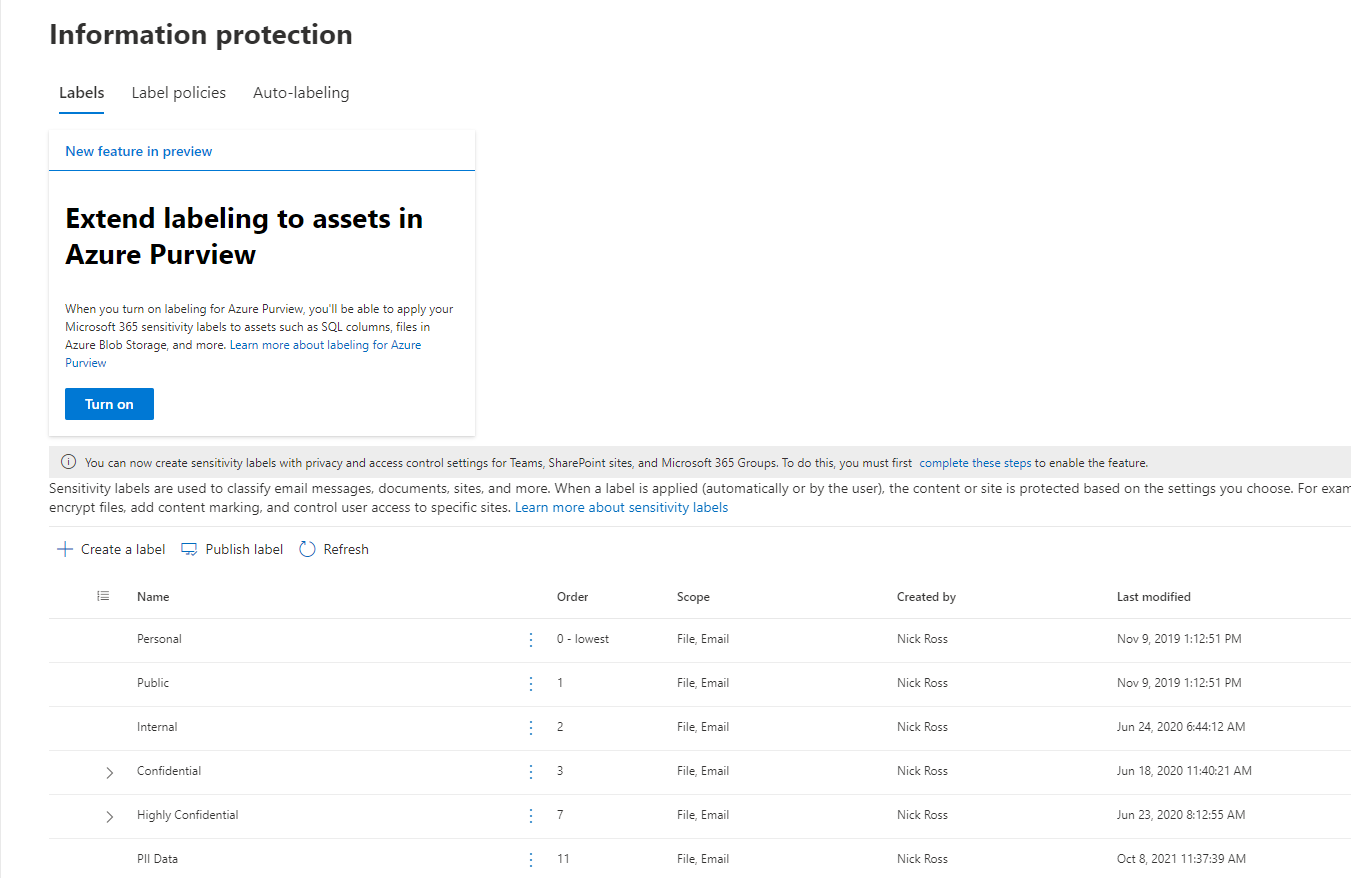
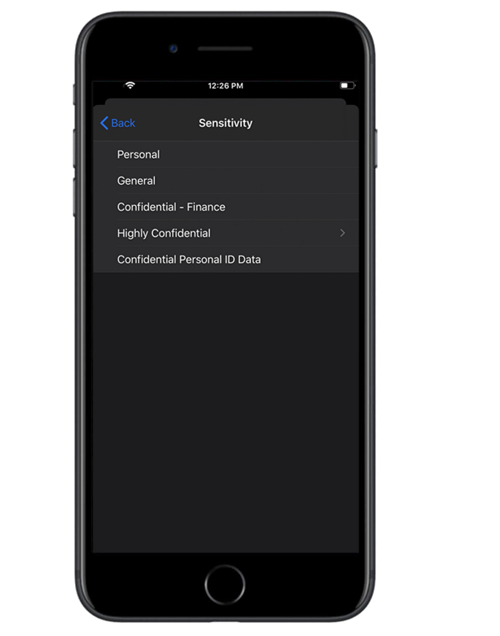
Here within the Microsoft 365 Compliance Portal, we have the ability to create labels for an organization. Microsoft provides you a default label-set which includes various categories users could leverage to tag documents and emails they interact with. Each label is paired with a policy that determines the controls that will be put into place. This includes things like if encryption will be applied, who has access to this content within the organization, and if the content is able to be shared to external users. Auto-labeling is another powerful feature that can auto-label documents based on sensitive information that is detected. An example of this is discovering documents that have social security numbers in them and automatically applying a highly confidential label. The benefits here are two-fold where you can reduce human effort to manually classify documents as well as avoid human error in applying these labels when new documents are created with sensitive content.
End-User Experience
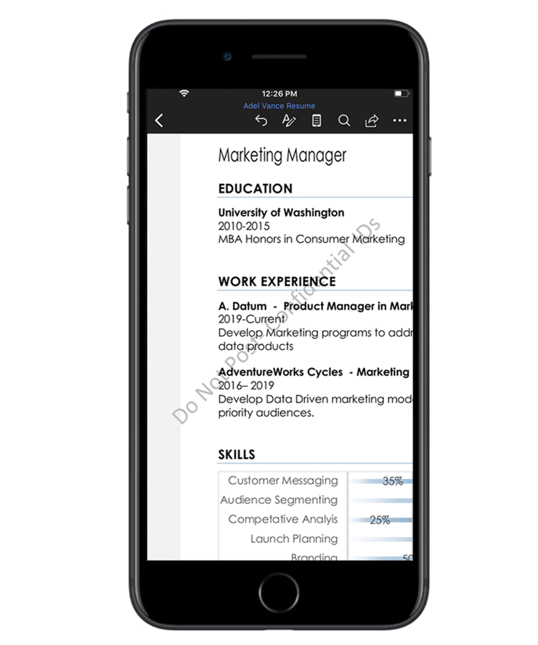
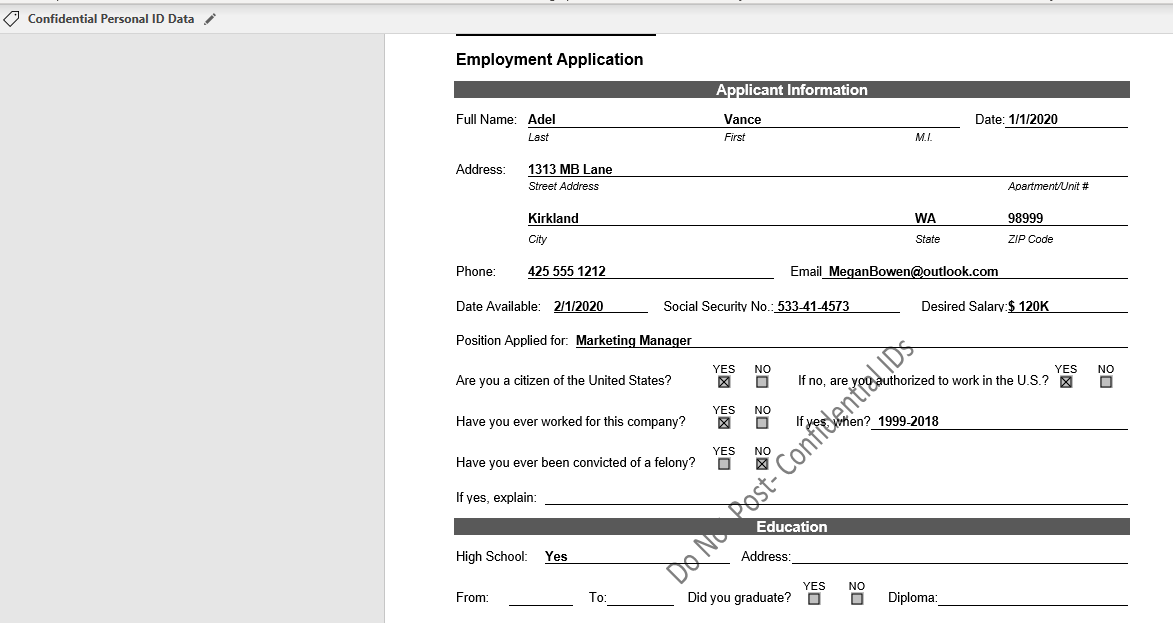
For the end user, lets start out with the mobile experience. Here we have Adele who is viewing a sensitive document in word on her cell phone. Leveraging Information protection, Adele is able to apply a sensitivity label to the document of confidential.
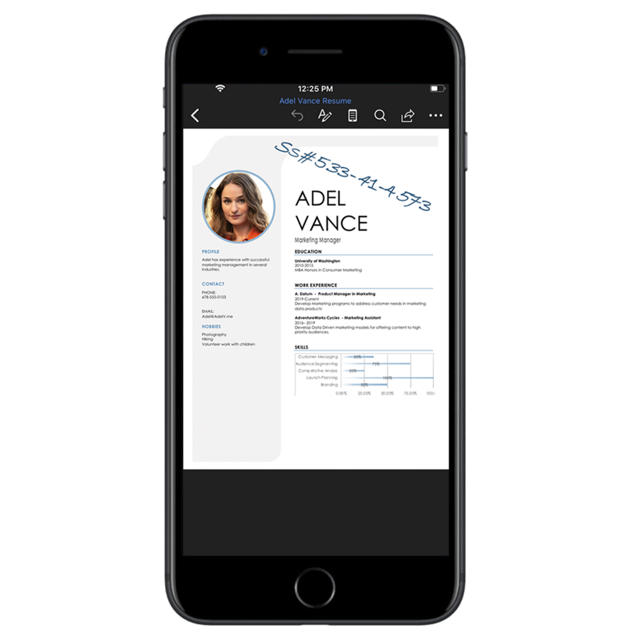
Notice how there is now a watermark on the document which relates to the protection being applied. Having this watermark should also help to reduce accidental sharing of confidential data.
Next lets take a look at automatic labeling in action on the desktop version of word. Here we have an employee adding a social security number to a document.
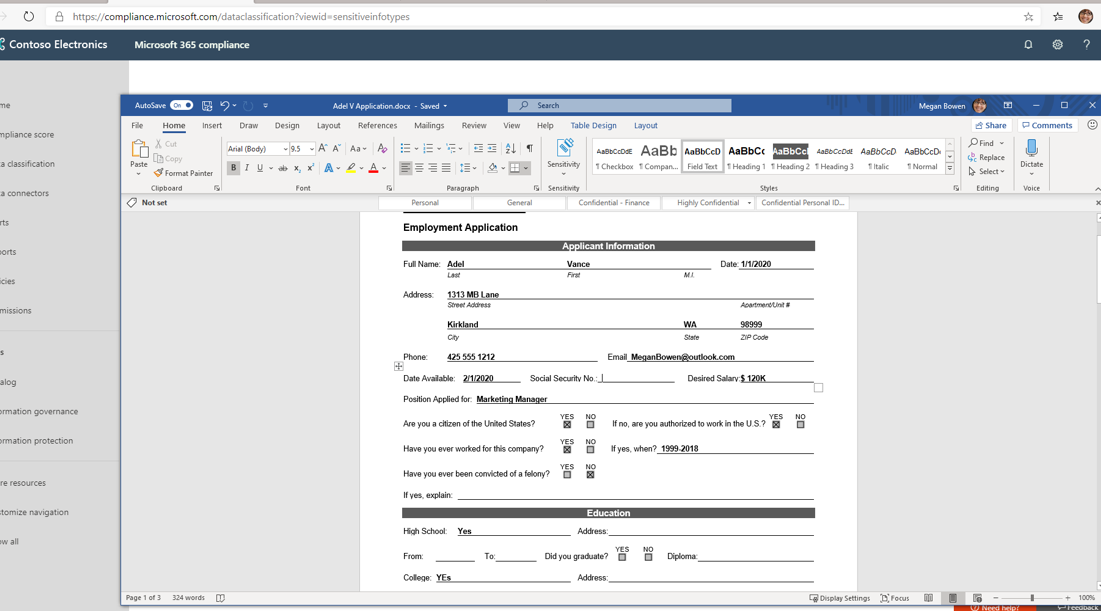
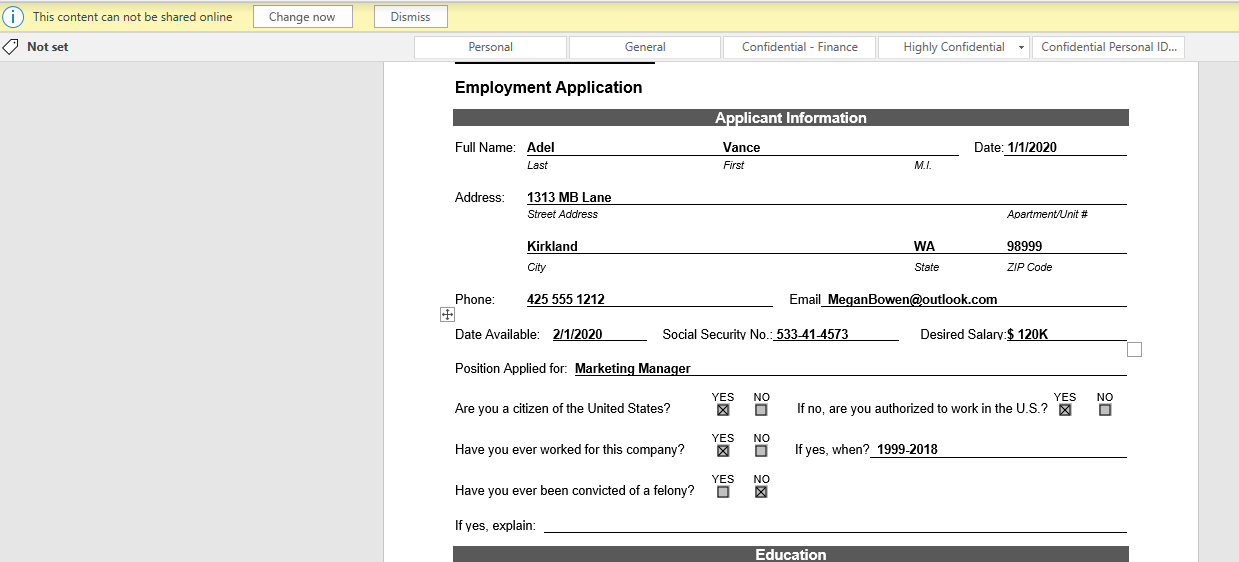
The user receives a notification once the SSN is detected letting them know that the document cannot be saved until the classification is changed. When the users clicks on change now, the confidential label is applied and the protections are put into place including the watermark like we saw in the previous example.
Conclusion
These are just a couple of examples here of the power of labeling in this solution. We will be diving into this in more depth in the coming blog post but that is all I wanted to cover in today’s article!