In this article, I am going to be walking you through an introduction of Microsoft’s Defender for Office 365 which comes part of the Microsoft 365 Defender offerings. Defender for office 365 contains some of the following high level features:
- Real-Time Detection and Prevention against malware/phishing
- Automated Investigation and Response
- Threat Hunting
- Attack Simulation Training
- Preconfigured Policies
- Correlated incidents with Microsoft Defender
Licensing
Defender for Office 365 can be purchases standalone or it is bundled into certain offerings. For SMB, Defender for Office 365 Plan 1 is also included with the Microsoft 365 Business Premium offering which you could be leveraging today.

Feature separation:
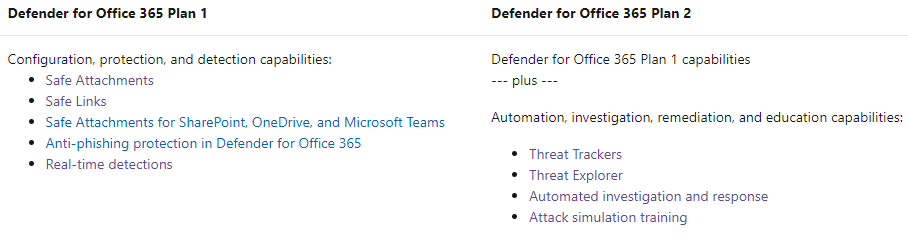
Overview
Microsoft Defender for Office 365 is a powerful toolset that safeguards your organization against malicious threats posed by email messages, links (URLs), and collaboration tools.
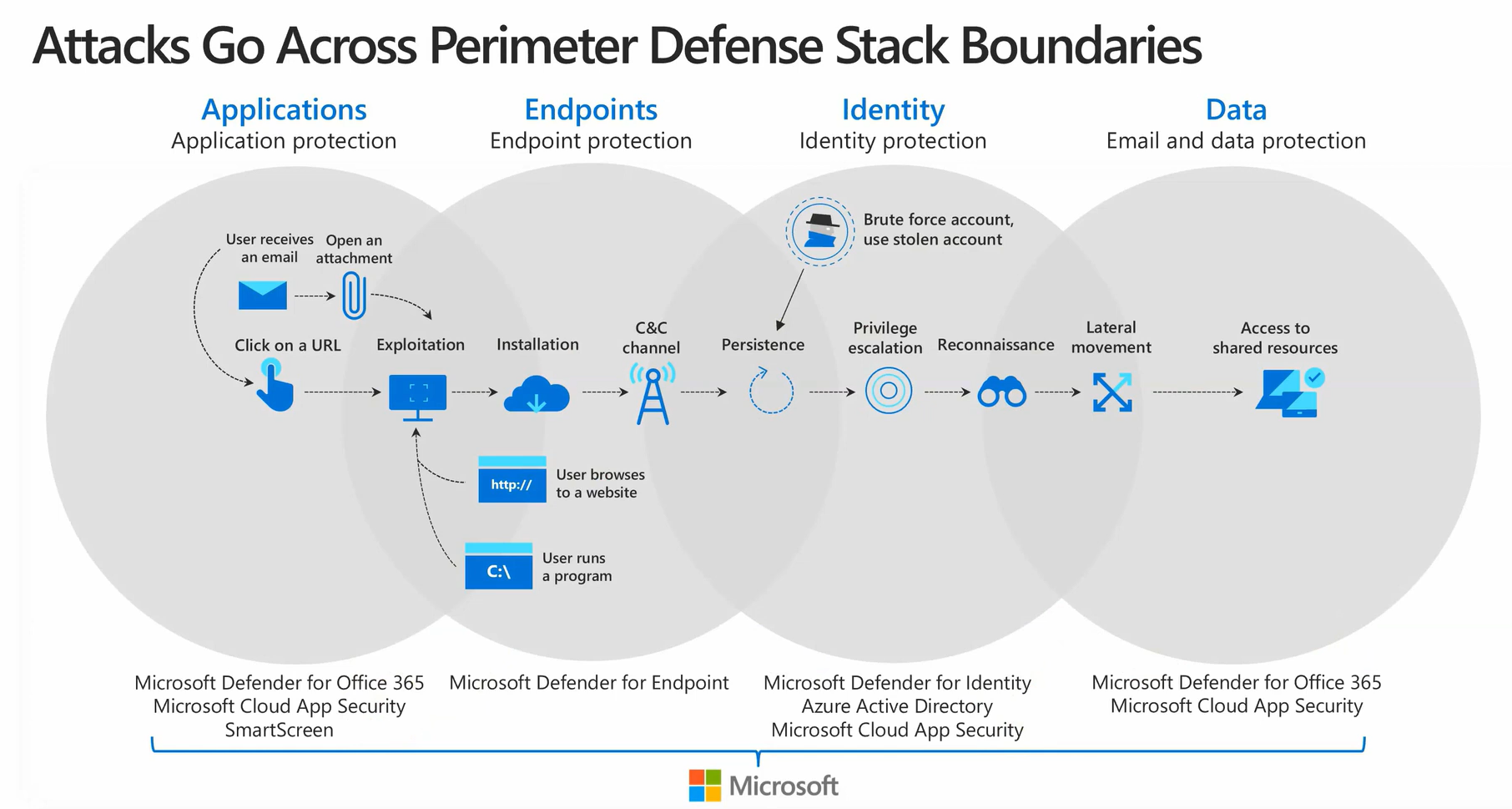
As with all of the Microsoft 365 Defender products, I like to show where this solution fits within a common attack chain so you get a better idea of the moving parts. Microsoft Defender for Office 365 is one of the primary initial defenses for email threats that could include malware or phishing attacks. This attack vector is one of the primary targets for someone to get an initial foothold within your organization.
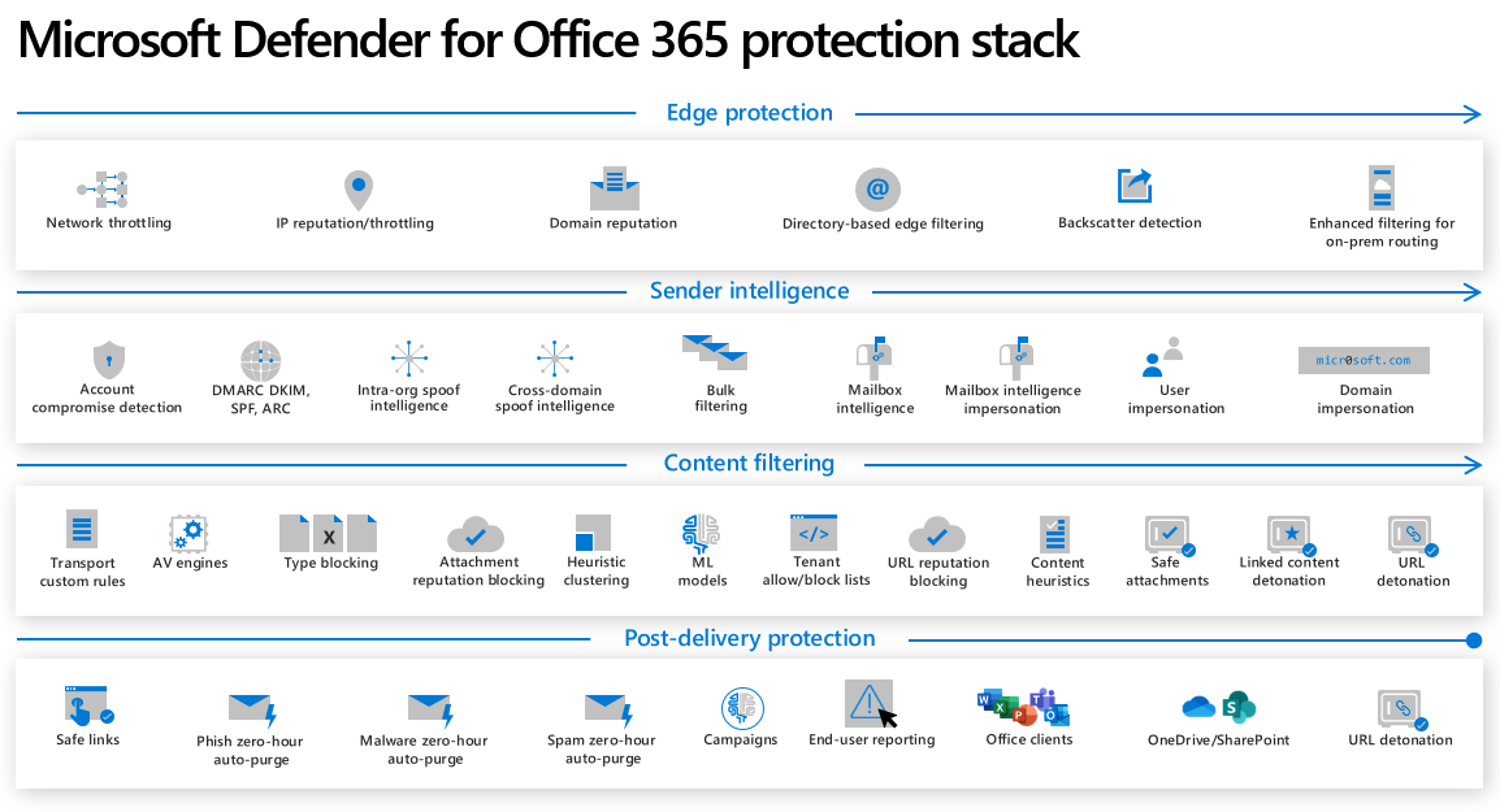
The Defender for Office 365 stack includes many layers of Protection. Combined with Exchange Online Protection, it can provide a powerful defense against all types of sophisticated attacks. The edge protection layer is something that can be more easily by based now so newer technologies are needed to help protect users. I key piece to note here is that these protections can be outside the organization AND also inside from users who may already be compromised through other attack vectors. I will not be going through all of these pieces today but you can see how Defender for Office 365 is doing all kinds of prevention and detection both pre and post delivery of mail.
Defender Security Center
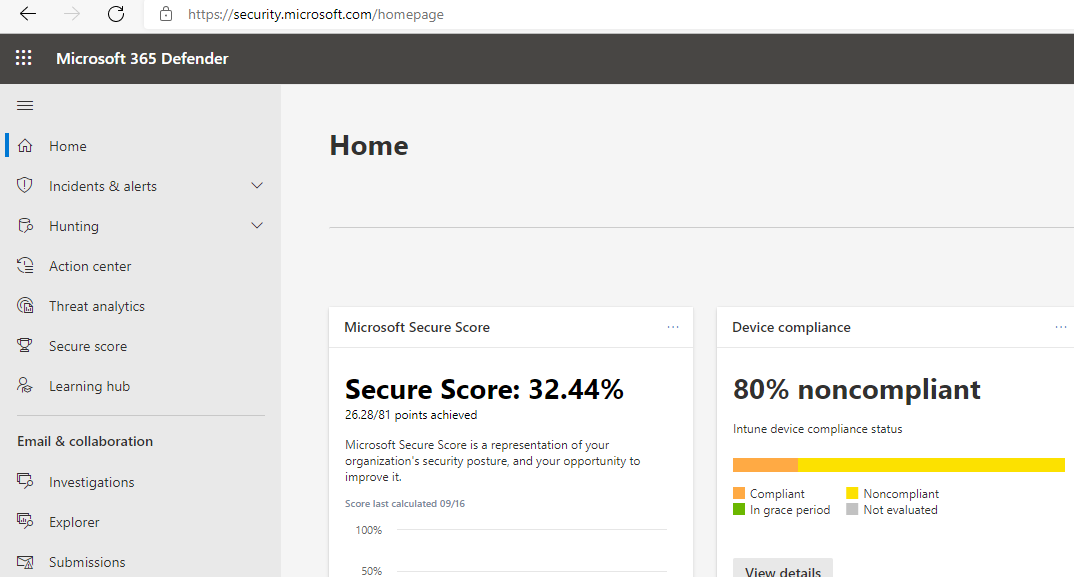
Microsoft recently announced a unified experience for all of the Defender products under security.microsoft.com. This experience is going to replace the legacy Security and Compliance Center you may be familiar with. Let’s take a look at each section within the Defender Portal.
1. Investigations
Most of the Defender for 365 features will be found here under Email and Collaboration. Investigations can be conducted automatically by Defender for Office 365 or when certain events occur like a user reporting an email as phishing. Defender does a through analysis and checks things that you may do as well like forwarding rules, delegated access rights but also things that you have never been able to before like Behavioral anomalies. It performs all of these task in about 10 minutes and gives you a full report of the results.
2. Explorer
The explorer tab can be used to hunt for threats within your organization. Here you are able to trigger investigations based on queries you create. Queries can be saved so that you can run them on demand in the future.
3. Submissions
Emails, Files, and URLs can be submitted to microsoft for further analysis. Users can also report messages like they think are malicious as well.
4. Review
Many of the default security settings will place malicious or high confidence phishing emails in quarantine. Here is where you can review those messages and release them on demand if you feel like it was a false positive.
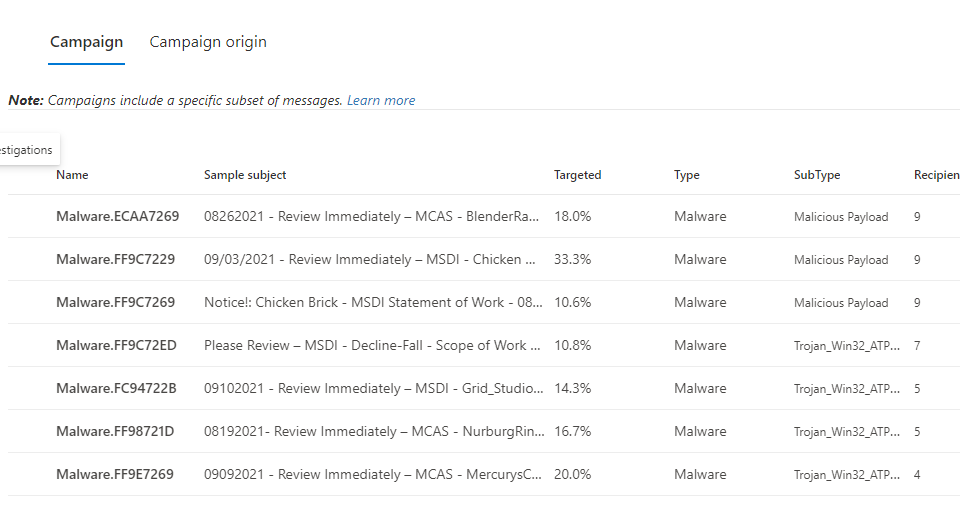
5. Campaigns
Common Campaigns can be tracked and you can review stats about the full scope of the campaign including how things were remediated and how end users interacted with the campaign.
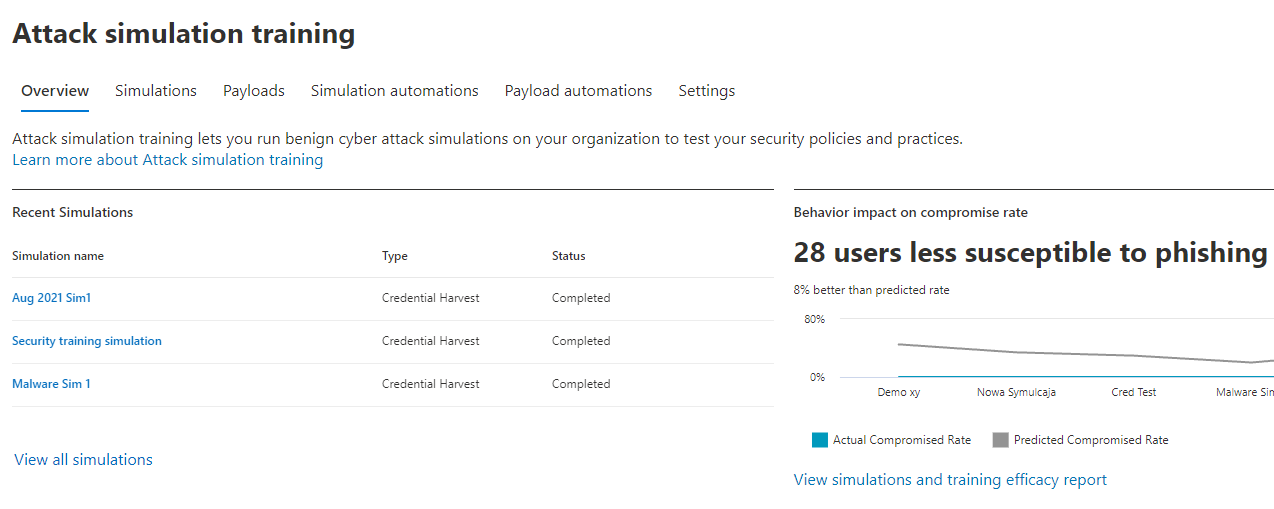
6. Attack Simulation Training
Attack simulations can be conducted within the organization to help users become less susceptible to common social engineering techniques.
7. Policy Configuration
Policies can be created to help protect against malware, spoofing, and phishing across your organization. These settings include safe links and safe attachments. You can also configure custom rules to help with sender authentication such as DMARC and DKIM records.
8. Correlated Incidents with Microsoft 365 Defender
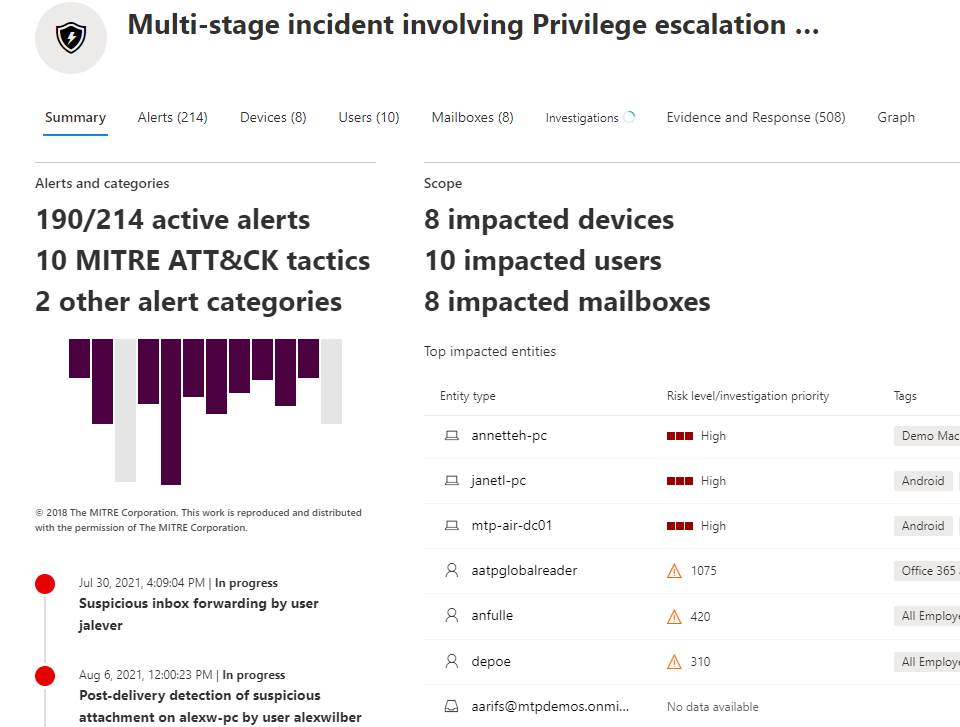
Finally, Defender for Office 365 is natively integrated in the other Microsoft Defender Products which means you get alerts that end up getting correlated into larger incidents. Here we can click into an incident and see that part of this attack timeline was an indicator coming from Defender for Office 365 where a suspicious inbox forwarding rule was created. This alert isolated may have not led to conclusions of the broader attack. This is the really powerful part about the integration between these products in Microsoft 365 Defender.
Summary
Defender for Office 365 can be a powerful offering for detecting and preventing attacks through email. I would recommend starting to leverage these features, especially if you already have a plan that includes it like M365 Business Premium. I would also evaluate whether the Plan 2 offering is something you could upsell your customers on, specifically for the Attack simulation training component.
