Microsoft Teams adoption has skyrocketed over the past year. This may seem like an obvious statement but I don’t just mean chat and video capabilities. Teams is becoming the central hub to interact with apps, share files, and perform daily tasks with members inside and outside the organization.
Microsoft is putting the most development effort into Teams. As an MSP, it is hard to keep up with all these changes, especially ones that might open up security and compliance risks. In this article, I will be providing my top 5 tips for securing Microsoft Teams.
1. Limit Guess Access
Starting February, 2021 Microsoft turned on guest access as a default setting in all new tenants. This means that Team owners can add external uses to any Teams channel. You should have a formal request process defined for adding external guest users to Teams channel where users submit business justification. Once you enable guest access, you can control the settings for the access rights that user has within the channel. Guess access should always be limited for a certain time period for security and compliance reasons.
Compliance Controls
- NIST CSP DE.CM-7
- NIST SP 800-53 Rev. 4 AU-12, CA-7, CM-3,
- CM-8, PE-3, PE-6, PE-20, SI-4
- HIPAA Security Rule 45 C.F.R. §§
- 164.308(a)(1)(ii)(D)
- 164.312(b)
- 164.314(b)(2)(i)
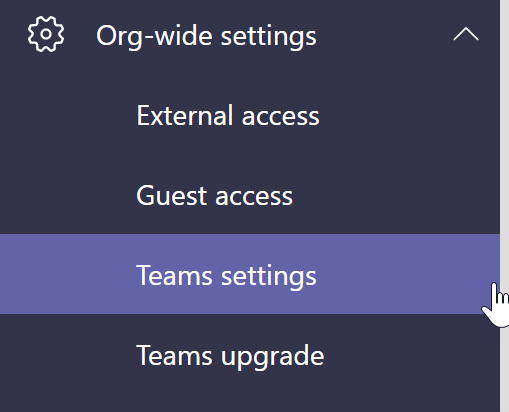
In the Teams Admin Center, click on Org-wide settings>Guest Access
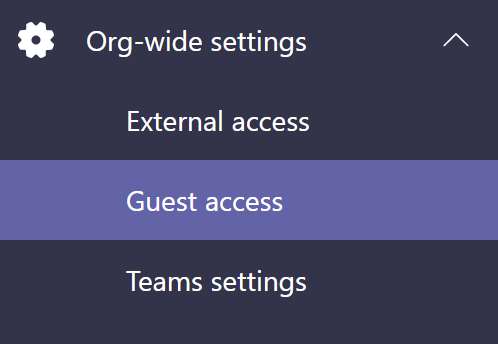
Review the settings. Notice that you can limit what guest can do in Teams.
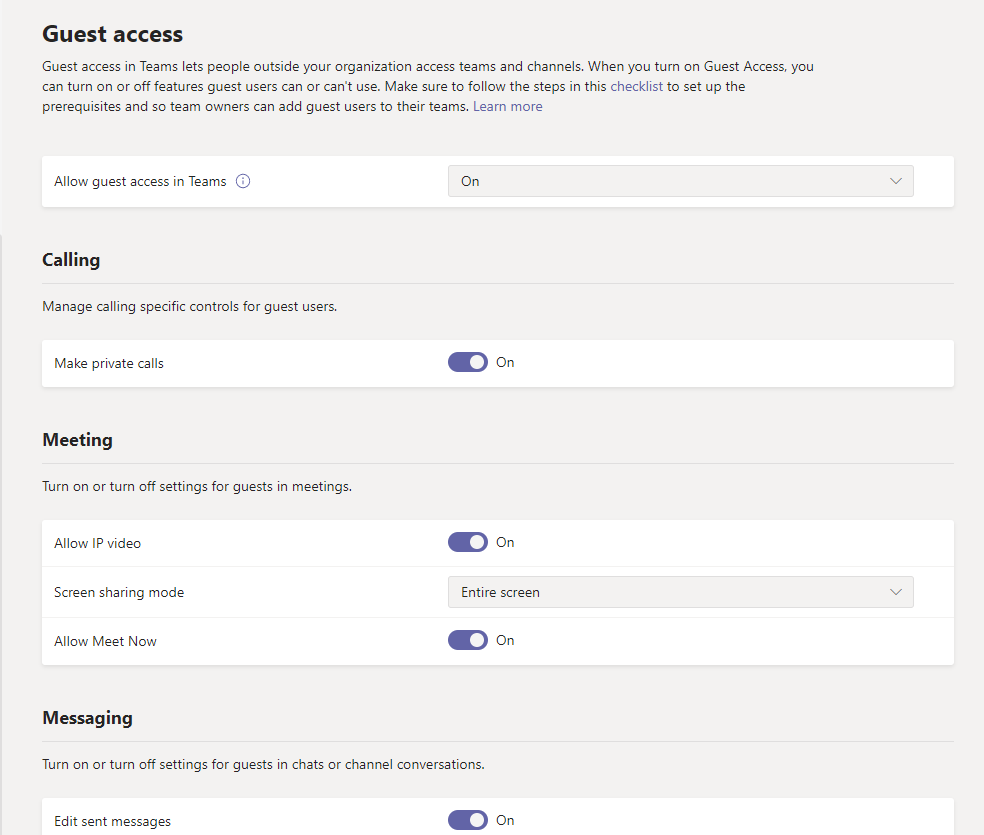
If Guess access is turned on, then owners can send invites to external participants
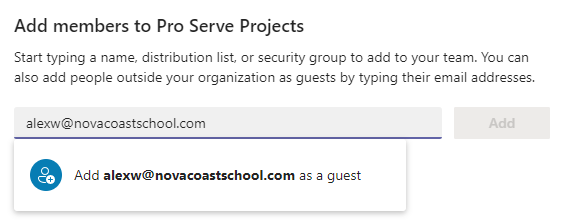
There are a few different ways in which you can manage this access. In Azure Active Directory, limit the domains for external collaboration and configure other settings. Admin Center>Azure Active Directory>Users>User Settings>Manage external collaboration settings
You can also create a new alerting policy in the Security and Compliance center so that you can be notified when a new sharing invitation has been accepted
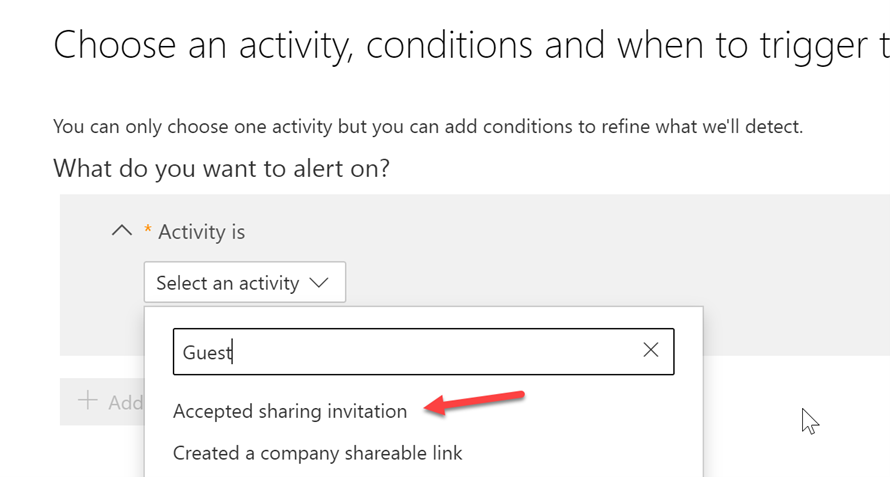
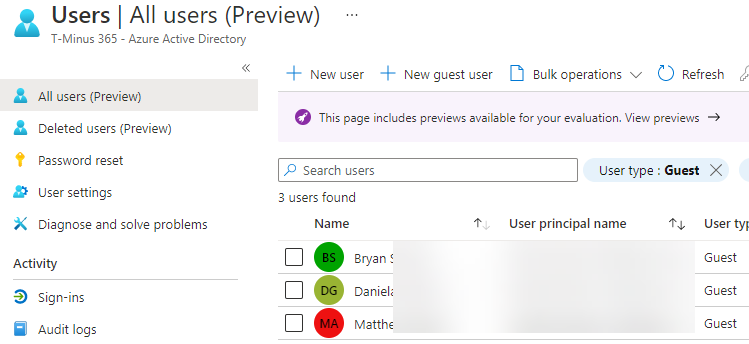
Additionally, you can review guest users in the Azure Active Directory portal on a regular cadence
2. Block External Access
You should not allow your users to communicate with Skype or Teams users outside your organization. While there are legitimate, productivity-improving scenarios for this, it also represents a potential security threat because those external users will be able to interact with your users over Skype for Business or Teams. Attackers may be able to pretend to be someone your user knows and then send malicious links or attachments, resulting in an account breach or leaked information
Compliance Controls
- NIST CSP DE.CM-7
- NIST SP 800-53 Rev. 4 AU-12, CA-7, CM-3,
- CM-8, PE-3, PE-6, PE-20, SI-4
- HIPAA Security Rule 45 C.F.R. §§
- 164.308(a)(1)(ii)(D)
- 164.312(b)
- 164.314(b)(2)(i)
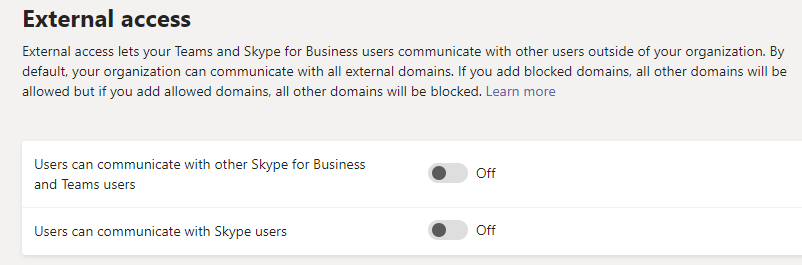
In the Teams Admin Center click Org-Wide Settings> External Access. Here you will turn the toggles off.
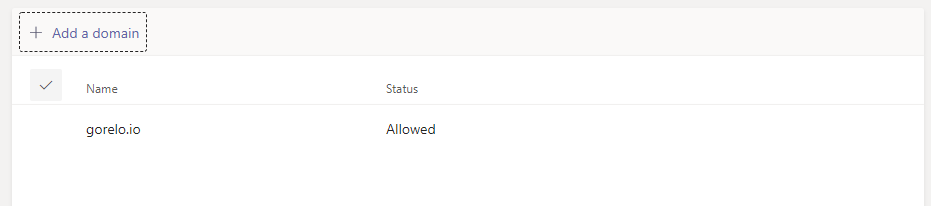
You can whitelist certain domains. This allows users to discover external users part of this domain and collaborate with them. This allows you to control the domains that users can collaborate with. Ensure that you have a proper, communicated method of how users can make request to collaborate with external organizations
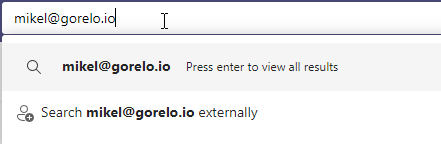
Users who search for external users in teams will see the following. If you have whitelisted the domain, the user will be able to add the user into a chat. If you have not they will get a message stating that “your organizations are not set up to talk to each other.
3. Turn off File Sharing and File Storage Options
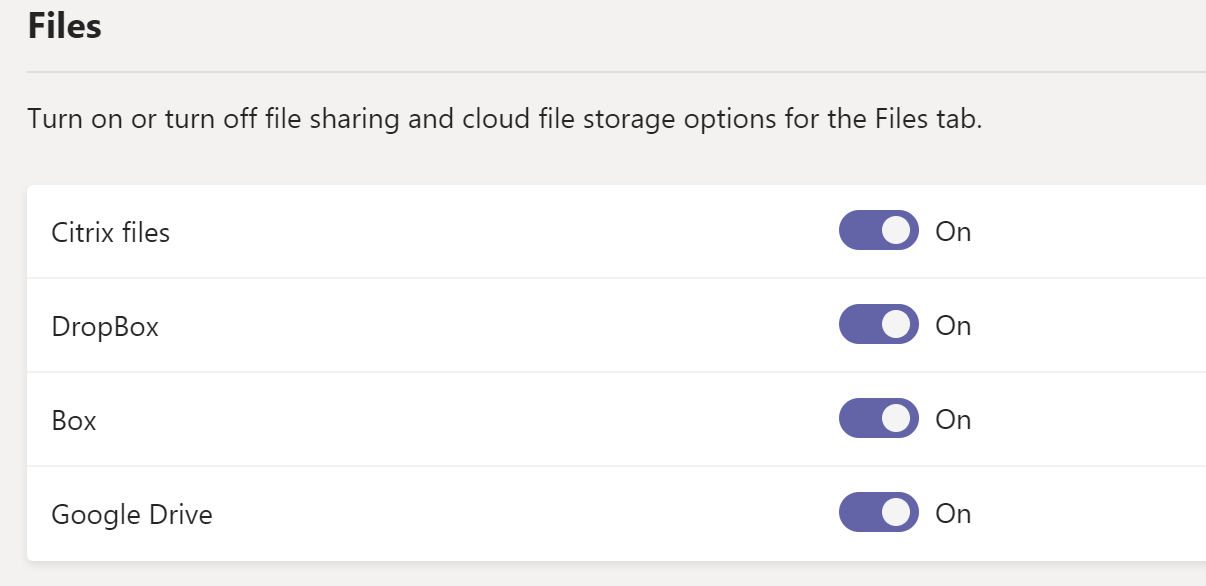
By default, users can add external 3rd party storage providers like Google and DropBox to their Teams channels for file storage. Only managed, trusted providers should be allowed for data loss prevention purposes
Compliance Controls
- NIST CSF PR-DS-5
- CCS CSC 17
- COBIT 5 APO01.06
- ISA 62443-3-3:2013 SR 5.2
- ISO/IEC 27001:2013 A.6.1.2, A.7.1.1,
- A.7.1.2, A.7.3.1, A.8.2.2, A.8.2.3, A.9.1.1,
- A.9.1.2, A.9.2.3, A.9.4.1, A.9.4.4, A.9.4.5,
- A.13.1.3, A.13.2.1, A.13.2.3, A.13.2.4,
- A.14.1.2, A.14.1.3
- NIST SP 800-53 Rev. 4 AC-4, AC-5, AC-6, PE19, PS-3, PS-6, SC-7, SC-8, SC-13, SC-31, SI-4
- HIPAA Security Rule 45 C.F.R. §§
- 164.308(a)(1)(ii)(D), 164.308(a)(3),
- 164.308(a)(4), 164.310(b), 164.310(c),
- 164.312(a), 164.312(e)
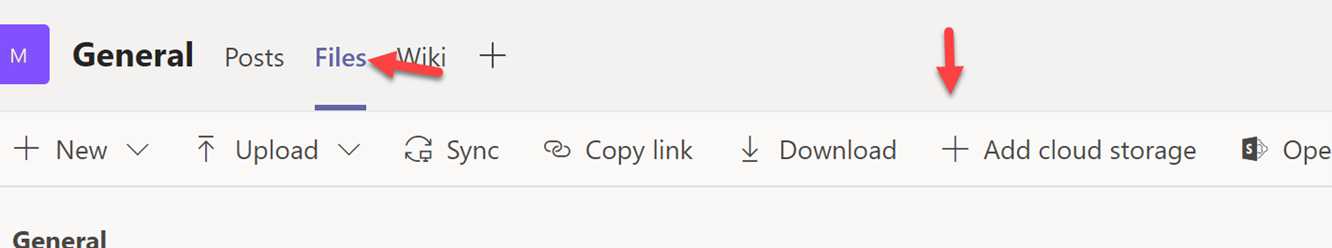
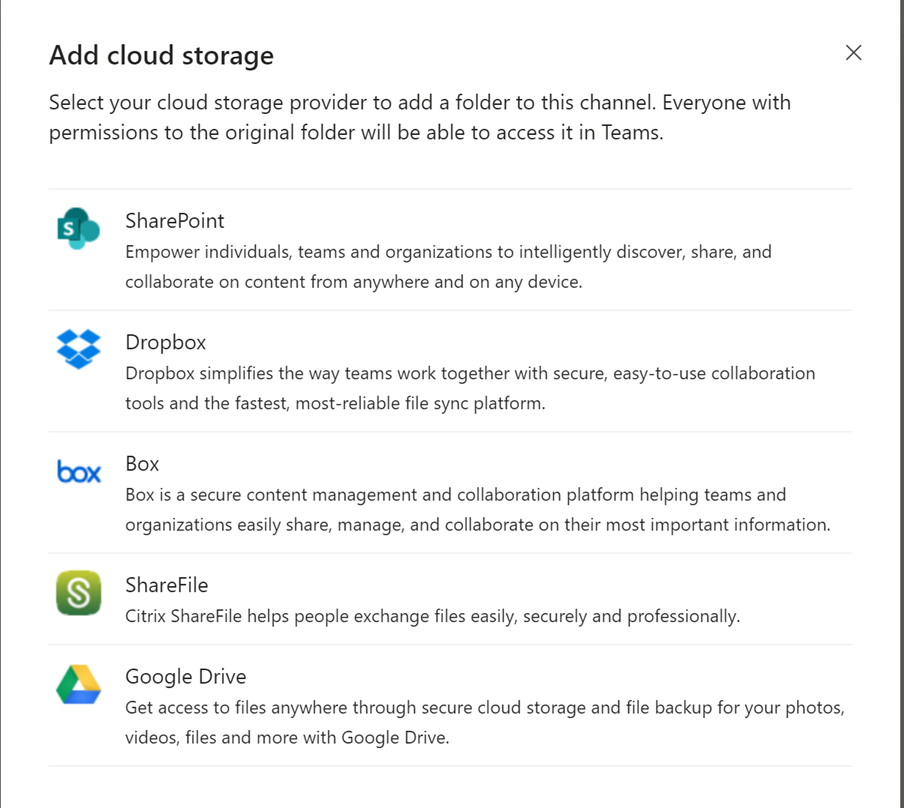
In the Teams Admin Center, Click Org-wide settings>Teams Settings
Scroll down to the Files section and un-toggle each provider that is not managed by the company:
4. Block 3rd Party Applications
By default, all users have access to the Teams app store which contains applications published by Microsoft and other 3rd parties. While we do not want to inhibit productivity, we do want to ensure we are preventing data loss and shadow IT at the organization. Any of these apps can be added to a Teams channel and users could begin to share corporate data back and forth with applications that are unmanaged. It is recommended that you whitelist applications that users can add and create a formal request process for additional applications
Compliance Controls
- NIST CSF PR-DS-5
- CCS CSC 17
- COBIT 5 APO01.06
- ISA 62443-3-3:2013 SR 5.2
- ISO/IEC 27001:2013 A.6.1.2, A.7.1.1,
- A.7.1.2, A.7.3.1, A.8.2.2, A.8.2.3, A.9.1.1,
- A.9.1.2, A.9.2.3, A.9.4.1, A.9.4.4, A.9.4.5,
- A.13.1.3, A.13.2.1, A.13.2.3, A.13.2.4,
- A.14.1.2, A.14.1.3
- NIST SP 800-53 Rev. 4 AC-4, AC-5, AC-6, PE19, PS-3, PS-6, SC-7, SC-8, SC-13, SC-31, SI-4
- HIPAA Security Rule 45 C.F.R. §§
- 164.308(a)(1)(ii)(D), 164.308(a)(3),
- 164.308(a)(4)
- 164.312(a), 164.312(e)
In the Teams Admin Center, go to Teams Apps>Permission Policies>Global
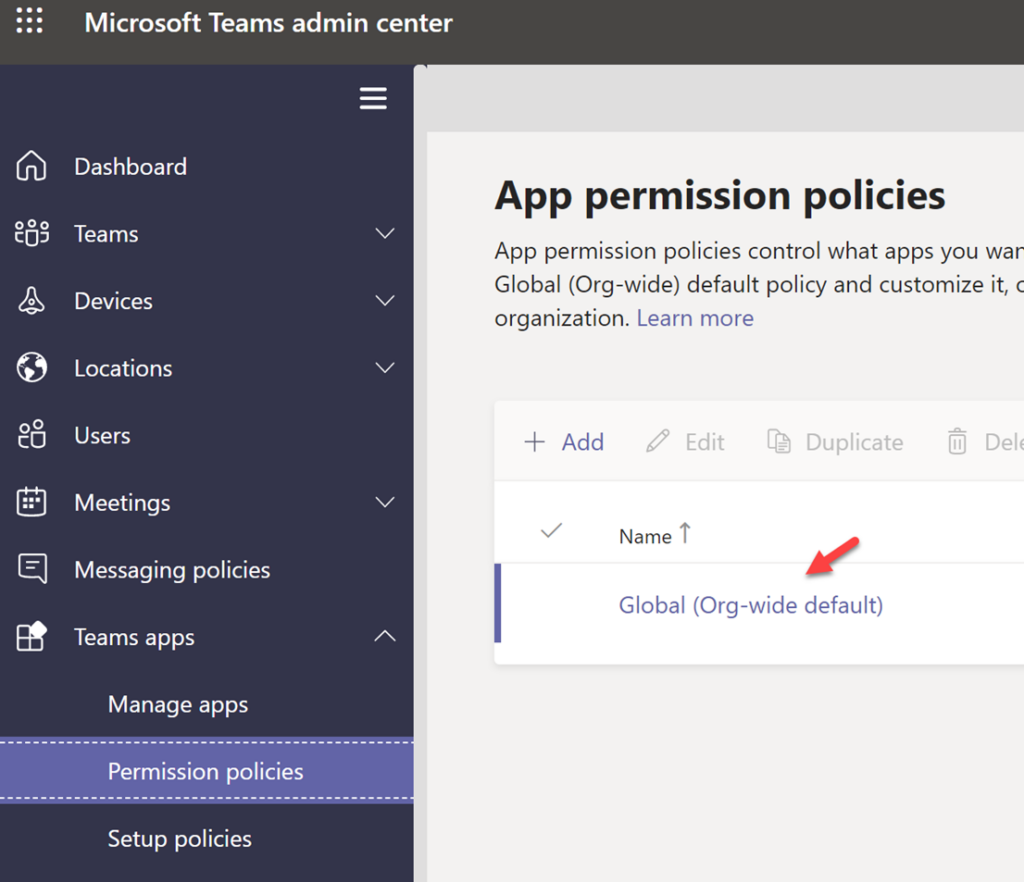
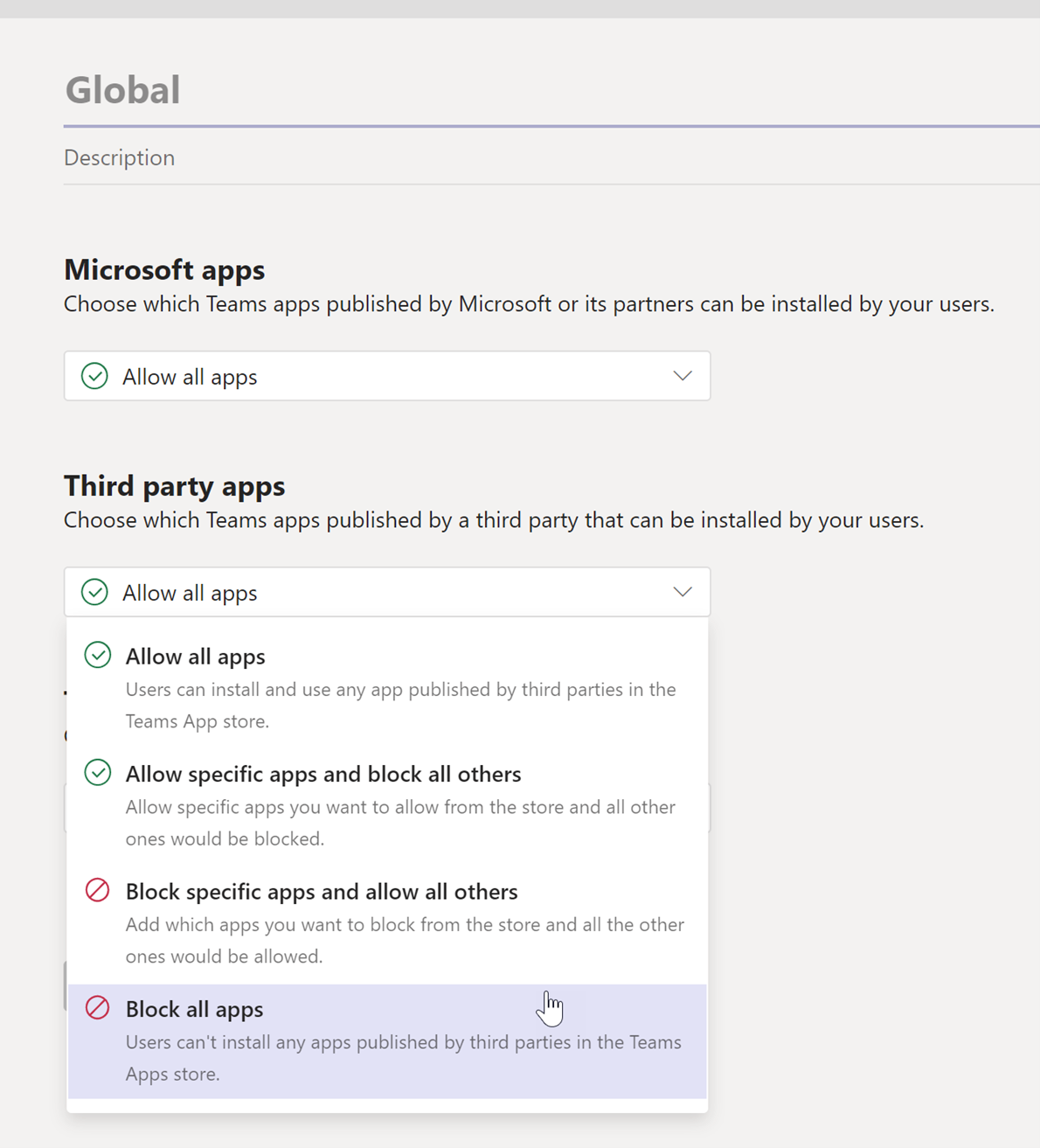
Choose to block all third-party applications or evaluate which apps you want to whitelist. Doing the same for Microsoft Applications is recommended
5. Restrict Users who can create Teams channels
Users within a tenant have the ability to create a public or private Teams channel by default. Behind the scenes, creating a Teams channel also creates an Office 365 Group and a SharePoint site with a document library that stores all documents shared within the Teams channel. Over time, if this is not managed, the environment could quickly get out of hand with the number of Teams channels being created. This could lead to data loss, insecure sharing of documentation, and overall confusion across the organization. I recommend limiting the creation of Teams channels to certain members within the organization and creating a formal request process for new channels. If you do not want to restrict this to a certain group, I recommend you at least set up expiration policies around Teams channels that are processed for review based on activity in the channel
Compliance Controls
- NIST CSF PR.PT-1
- CCS CSC 14
- COBIT 5 APO11.04
- ISA 62443-2-1:2009 4.3.3.3.9, 4.3.3.5.8,, 4.3.4.4.7, 4.4.2.1, 4.4.2.2, 4.4.2.4
- ISA 62443-3-3:2013 SR 2.8, SR 2.9, SR 2.10, SR 2.11, SR 2.12
- ISO/IEC 27001:2013 A.12.4.1, A.12.4.2, A.12.4.3, A.12.4.4, A.12.7.1
- NIST SP 800-53 Rev. 4 AU Family
- HIPAA Security Rule 45 C.F.R. §§
- 164.308(a)(1)(ii)(D), 164.308(a)(5)(ii)(C),164.312(b)
Microsoft has a whole article I will reference here that shows you the necessary steps to perform with Powershell to restrict the groups that can create Teams channels. After you run the script, all users who are not part of the group will not be able to create new channels:
Conclusion
These 5 tips can be used as a starter to hardening Teams environments across all of your customers. Please share with the community and provide some of the things you are doing to secure Teams as well.
