When I think about today’s remote workforce for MSPs (Managed Service Providers), conditional access policies can be incredibly useful in securing client environments. VPNs are being used now more than ever to connect securely to corporate resources. For this reason, using IP ranges as a named location in conditional access polices might not be the best approach.
Microsoft recently introduced a public preview of GPS-based named locations. With this new feature, admins can enhance their Conditional Access policies and determine a user’s true location with more accuracy. I recently tested this feature out and wanted to share my findings.
TLDR
- The solution is effective but is not very user friendly
- Every user must be the using Microsoft Authenticator app for this feature to work correctly.
- Every hour, the system will contact the user’s Microsoft Authenticator app to collect the GPS location of the user’s mobile device.
- The first time the user is required to share their location from the Microsoft Authenticator app, the user will receive a notification in the app. The user will need to open the app and grant location permissions.
- For the next 24 hours, if the user is still accessing the resource and granted the app permission to run in the background, the device’s location is shared silently once per hour.
- After 24 hours, the user must open the app and approve the notification. Every time the user shares their GPS location, the app does jailbreak detection (Using the same logic as the Intune MAM SDK). If the device is jailbroken, the location is not considered valid and the user is not granted access.
- A Conditional Access policy with GPS-based named locations in report-only mode prompts users to share their GPS location, even though they are not blocked from signing in.
Prerequisites
Every user must be the using Microsoft Authenticator app for this feature to work correctly. If you are using a 3rd party app, like DUO, this feature will not be available.
Configuration
1. In the Azure AD Admin Center > Security>Conditional Access>Named Locations> +Countries Location.
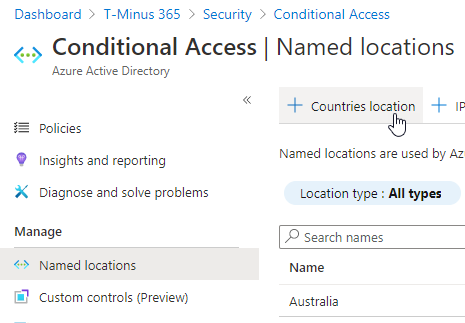
2. Select ‘Determine location by GPS coordinates” and your country
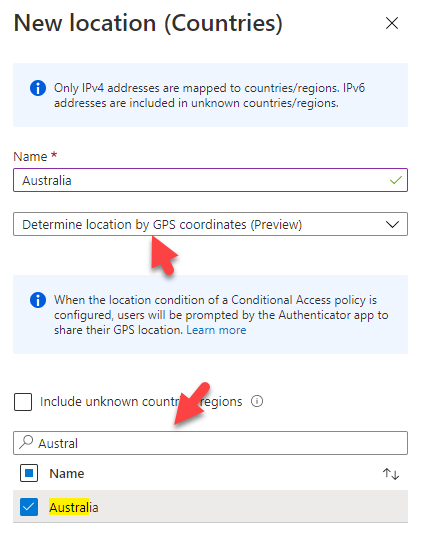
3. Save and then Click Conditional Access Policies. Create a new policy and scope it to certain users. Under Conditions, select Locations>Yes(Configure)>Exclude Selected Locations>Chose your location.
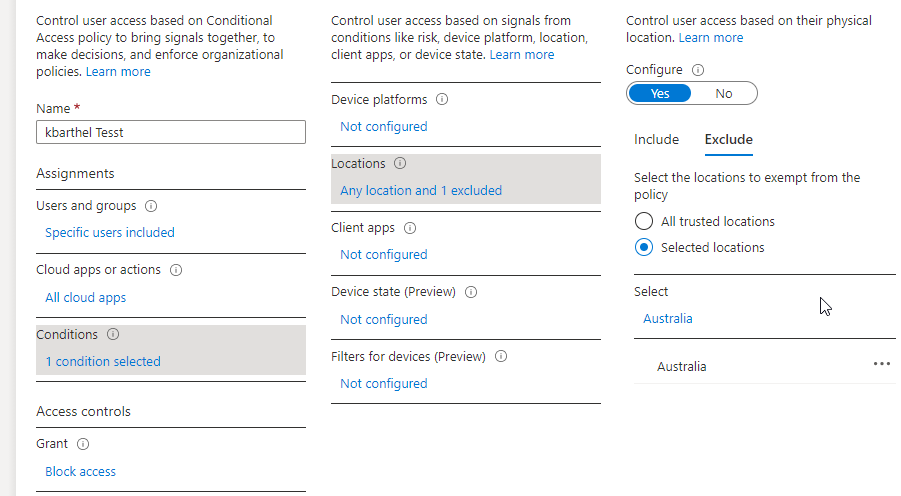
4. Block Access and chose report-only to test out this policy.
End User Experience
After the CA policy is in report-only or on, the next time the user signs in they will be prompted with the following screen:

On their mobile device in the Authenticator app, they will be prompted with the following(iOS):
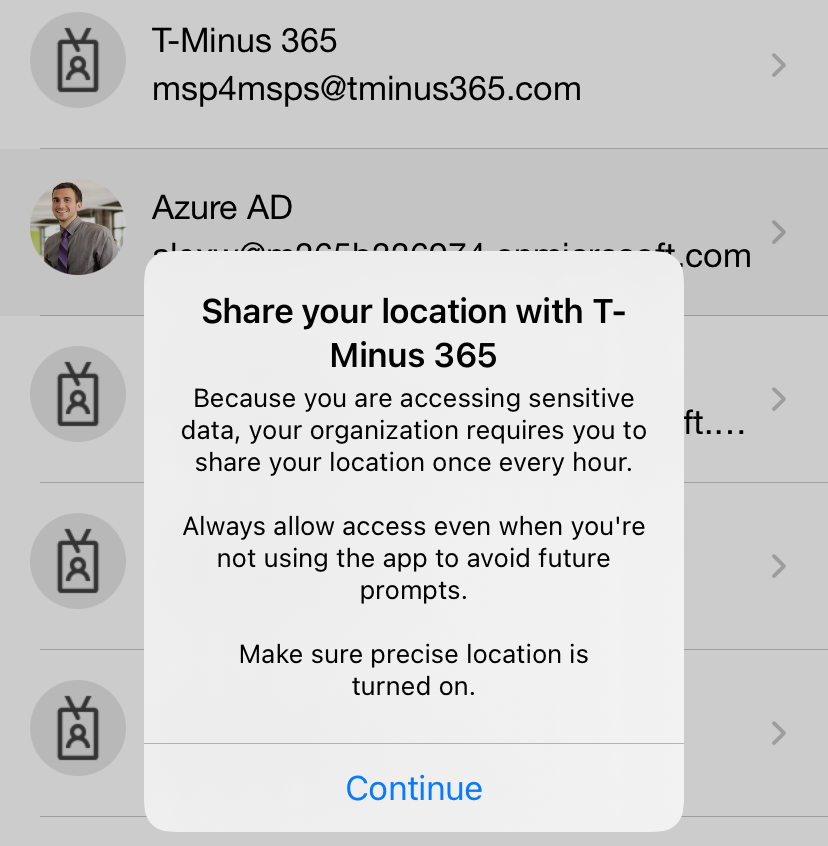
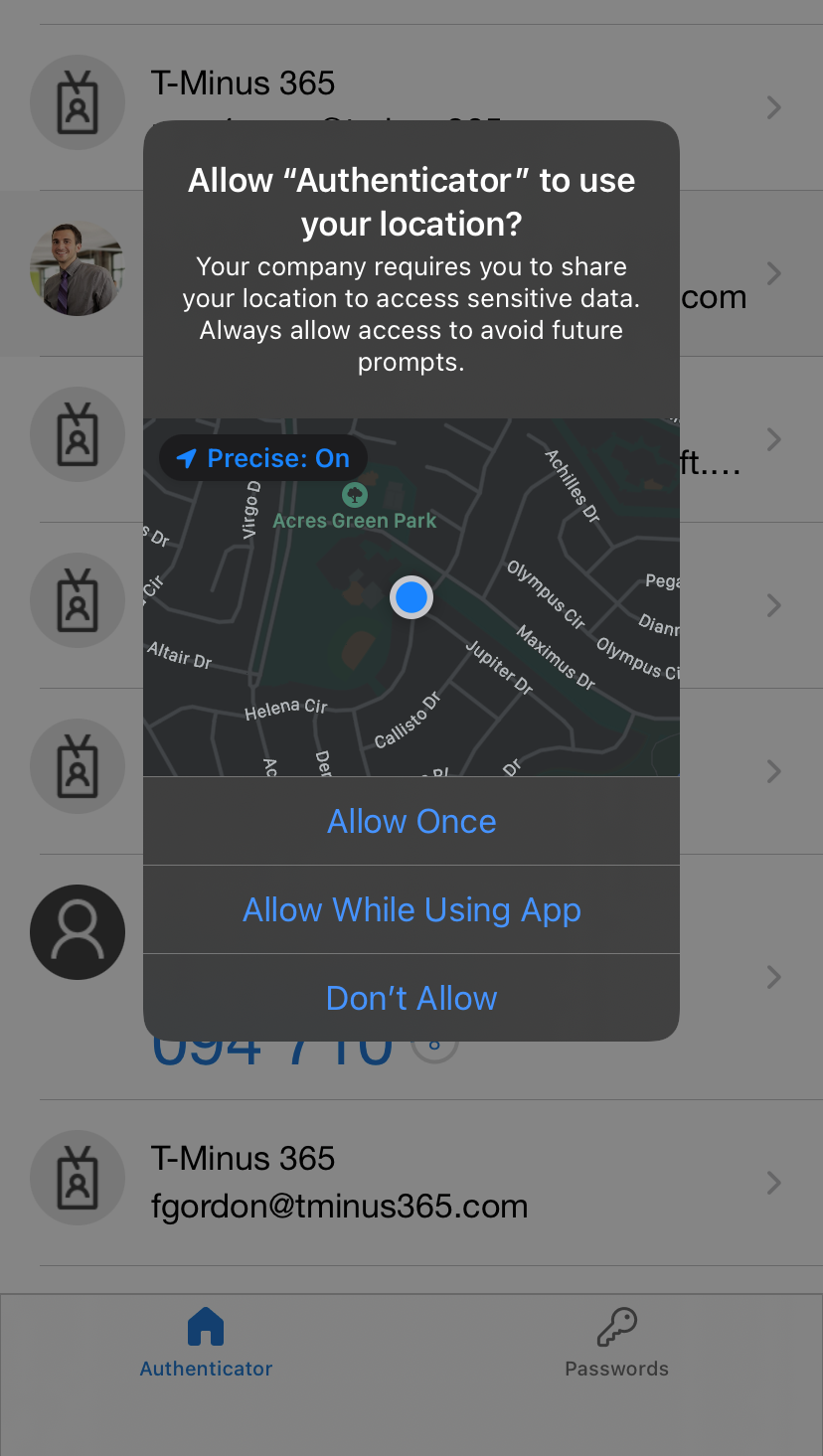
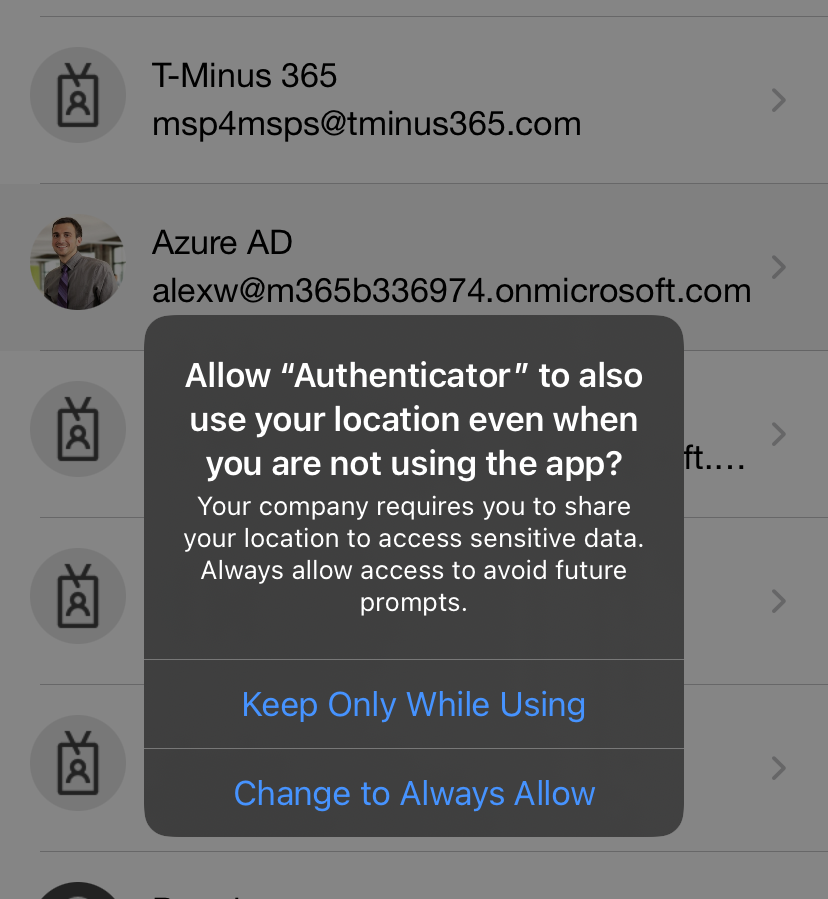
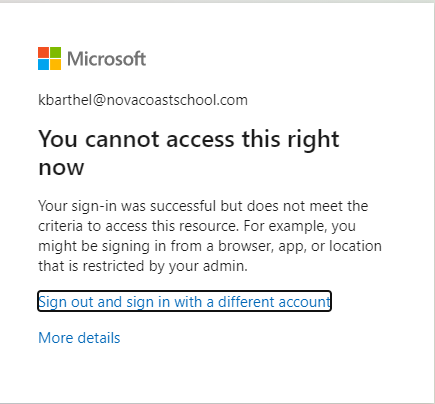
If a user choses the “Keep Only While Using” selection, they will be prompted ever 24 hours to reconfirm their location. If they chose “Change to Always Allow” they will only be prompted on time. Every time the user shares their GPS location, the app does jailbreak detection (Using the same logic as the Intune MAM SDK). If the device is jailbroken, the location is not considered valid and the user is not granted access. A user blocked from sign in will see the following:
Conclusion
I would strongly recommend some communications to end user before implementing this policy. I would also probably only use this on apps with confidential or sensitive data as it get very disruptive and annoying very quickly as an end user with the 24 hour check in. If you set up this CA policy there is not much propagation time at all. If you are not getting your test results right away it is likely you have configured the policy incorrectly.
